Last Updated: 5/29/2019
Eric Sifford, security researcher with Armor’s Threat Resistance Unit (TRU), found new tweets on Saturday, May 25, 2019 and on Tuesday, May 28, 2019 from a Twitter account , which appears to be connected to the City of Baltimore ransomware attackers. Both tweets were directed squarely at Baltimore’s mayor, Bernard C. “Jack” Young. See Images 2 and 3.
“These recent tweets, apparently from the alleged City of Baltimore hacker(s) or their representative, are telling,” said Sifford. “The initial tweet from this Twitter account on May 12 included what looked to be usernames, passwords, and other sensitive-looking, internal documents from the City of Baltimore. However, that tweet apparently failed to achieve the response the hacker(s) desired, as the newest tweets take things a step further.” The tweet on May 25 taunts and chastises the city’s Mayor for not paying the ransom. See Image 2. The tweet on May 28 offers to decrypt one of the city’s computers for free if the Mayor sends hostnames of 5 affected machines. See Image 3.
“It is clearly an effort by the hacker(s) to prove they can decrypt the city’s files,” continued Sifford. “This might be an opportunity for the Mayor and Baltimore’s incident responders to determine if the threat actors truly have the capabilities to unlock their data. As a cybersecurity expert, I generally recommend against paying a ransom; however, each case is unique in its totality, and I understand sometimes an organization’s leadership may decide their best option is to pay.”
The Twitter profile (which contained “Robbinhood” in its profile name) tagged a Maryland State Senator, six City of Baltimore council members, various news outlets, and other city leaders
The Bitcoin wallet address in the Baltimore ransom note is listed as 14yos7dpe4bx3imnoGVUcMsNBwU1hLutfj. As of Wednesday, May 29, there have been no inbound or outbound transactions to this wallet. An additional Bitcoin wallet address, reported to be connected to the Robbinhood ransomware, also shows no inbound or outbound transactions. That wallet address is: 132wg6kkJJ4MpNKnuhVoptYPmYHf6C5xHE
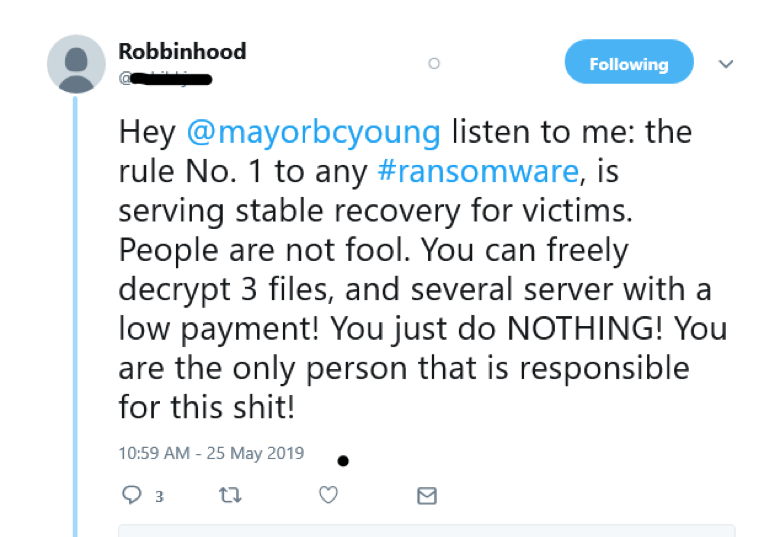
Image 2:Saturday, May 25 tweet from Twitter user who could be the threat actor behind the Baltimore ransomware attack.
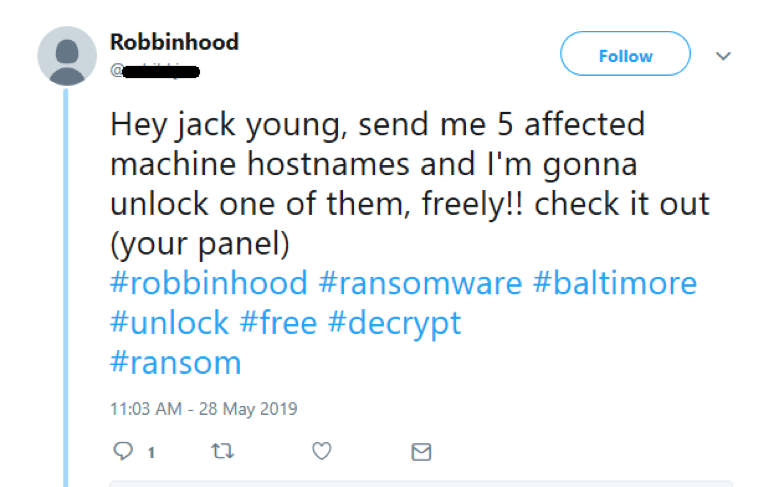
Image 3: Tuesday, May 28 tweet from Twitter user who could be the threat actor behind the Baltimore ransomware attack.
Post Appears to Taunt City Officials
Eric Sifford, security researcher with Armor’s Threat Resistance Unit (TRU) found that on Sunday, May 12, 2019 a newly created Twitter account posted usernames, passwords and other sensitive-looking, internal documents which appear to be related to the city of Baltimore. Armor chose not to reveal the Twitter handle at this time, so as to ensure the City of Baltimore has the opportunity to change the usernames and passwords in the Tweet should they be authentic. (See Image 1).
The Twitter profile included the name “Robbinhood” in its profile description. This is the ransomware which purportedly shut down portions of the city’s IT network. At this time, it is unclear whether the post is truly a message from the threat actors behind the Baltimore ransomware attack or a malicious prank from someone with access to internal documents relating to the city.
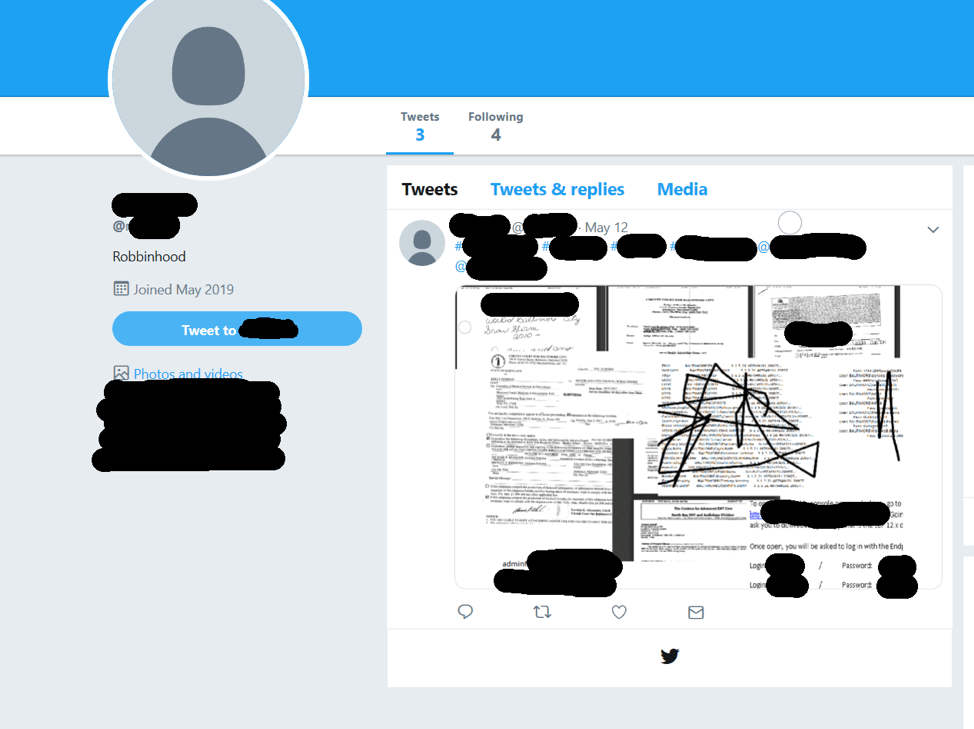
Image 1: Profile page for a Twitter user who could be the threat actor behind the Baltimore ransomware attack.
City of Baltimore, One of Over 20 Government Organizations, to Be Compromised by Ransomware in 2019
On Tuesday, May 7, news broke that the city of Baltimore had been hit for a second time in just over a year by ransomware. According to news reports, the city’s government computers were infected with ransomware, alleged to be a ransomware family known as Robbinhood.
Ransom Demanded of City of Baltimore
Armor, a global cloud security solutions provider, analyzed the ransom message which appeared on the city of Baltimore’s computer system (see image 2). It said the Robbinhood ransomware, used a file-locking virus that encrypts files to take them hostage. The note demanded payment of 3 Bitcoins (currently equal to approximately $23,267 @ 2:15 CST 5/14) per system, or 13 Bitcoins (equal to approximately $100,823 @ 2:15 CST 5/14) in exchange for decrypting all the city’s systems.
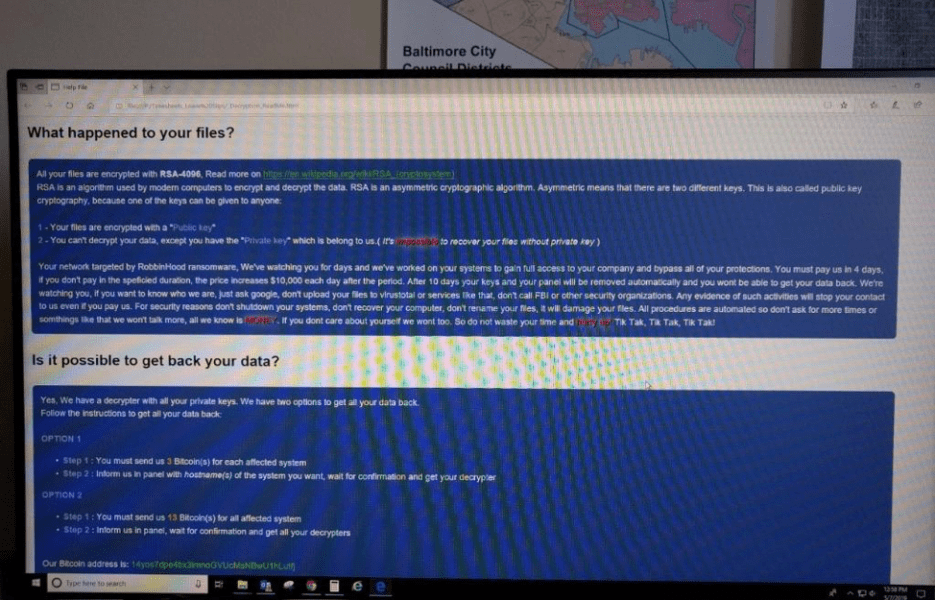
Image 2: City of Baltimore ransom note which appeared on the city’s computers Tuesday, May 7, 2019.
The Bitcoin wallet address in the Baltimore ransom note is listed as 14yos7dpe4bx3imnoGVUcMsNBwU1hLutfj. As of Tuesday, May 14th , there have been no inbound or outbound transactions to this wallet. An additional Bitcoin wallet address, reported to be connected to the Robbinhood ransomware, also shows no inbound or outbound transactions. That wallet address is: 132wg6kkJJ4MpNKnuhVoptYPmYHf6C5xHE.
Baltimore Ransom Note:
The Baltimore ransom note stated: “We’ve watching you for days and we’ve worked on your systems to gain full access to your company and bypass all of your protections.” It said that ransom must be paid within four days or the price would go up, and that after 10 days, the city would not be able to get its data back.
The note warned the city against calling the FBI, saying that would prompt the attackers to cut off contact. It also said that attempts to use anti-virus software would damage the city’s files. The ransomware’s procedures are automated, the note said, “so don’t ask for more times or somethings like that.”
“We won’t talk more. All we know is MONEY!” the note said. “Hurry up! Tik Tak, Tik Tak,
Tik Tak!”
How Did City of Baltimore Get Infected
How the ransomware initially infected the city of Baltimore’s computers has not been revealed. However, Armor’s Threat Resistance Unit (TRU) has observed in its protection of 1,200 clients worldwide that three of the most common infection vectors for ransomware are the compromise of “open” Remote Desktop Protocol (RDP) servers, exploit kits and malicious phishing emails.
City of Baltimore, One of Over 20 Government Organizations to Be Compromised by Ransomware in 2019
The City of Baltimore is one of 22 government organizations to be hit by ransomware in 2019. Armor has tracked the following ransomware attacks:
- Baltimore, MD–May 2019– Hit with what appears to be RobbinHood, the same ransomware which reportedly hit Greenville, NC. Baltimore is the latest high-profile attack. The city shut down most of its servers due to the infection, but critical services such as EMS, police, fire and 311 remained operational.
- Washington, PA–May 2019—Ransomware hit the city’s phone systems and servers. Nearly a week later, Mayor Scott Putnam stated they were “still trying to figure out what happened”, and “not sure what is going on”.
- Amarillo, TX – April 2019– The city of Amarillo TX was hit with ransomware impacting the County Clerk, District Clerk and Sheriff’s Office, encrypting files and emails.
- Cleveland Airport, OH – April 2019–A ransomware attack shut down administrative systems at Cleveland Hopkins International Airport, affecting email, payroll, and information systems.
- Augusta City Center, ME – April 2019–Malware locked up city servers and spread to additional devices in municipal operations, causing a reduction in system accessibility for a few days and the suspension of some services. No ransom payment was made, and no data was released.
- Stuart, FL– April 2019–A ransomware attack encrypted data on the city’s servers. The ransom demand was not paid, and staff rebuilt systems, but services were reduced over a period of days.
- Imperial County, CA –April 2019– Ransomware encrypted much of the county’s digital information and shut down the county’s online payment system, the clerk-recorder’s office, and the Department of Social Services, among others.
- Garfield County, UT –April 2019– A ransom payment by Garfield County, UT, was made so that they could recover data encrypted by a ransomware attack. The attack reportedly started after someone clicked on a phishing
- Greenville, NC – April 2019 – A ransomware attack in April 2019 caused the city of Greenville to return to using paper forms, after the threat actors shut down the city’s computer systems for over a week (purportedly also using the RobbinHood malware). The attack infected the city’s police and fire systems, financial systems, and email. In addition to servers, over 800 workstations needed to be checked for infection and 130 different systems needed to be repaired.
- Albany, NY –March 2019– A ransomware attack resulted in the suspension of some city services, although many operations continued to function. The attack impacted the records and marriage-certificate offices.
- Jackson County, GA – March 2019 – Hit by ransomware, the county paid a $400,000 ransom to the hackers to receive the decryption key. The ransomware forced the county to use paper and other manual methods to provide services.
- Schools System of Taos, NM –February 2019- Schools were infected by a ransomware attack. The criminal demanded a $5,000 payment for the decryption key. The ransomware was introduced to the system through a phishing email and shut down most of the school system’s digital services.
- Del Rio, TX – January 2019 –The Texas city was forced to use pen and paper when a ransomware attack knocked out the city’s servers. No ransom was paid.
- Atlanta, GA – March 2018 – The Atlanta ransomware attack in 2018 was one of the most highly publicized ransomware cases. Server access was blocked for six days, resulting in significant disruption and a costly fix. Estimates of the cost of the attack range on the low end $2.6 million to $17 million.
- Leominster, MA – March 2018 – The Leominster Public School System paid $10,000 in ransomware to retrieve files following an attack that encrypted files and froze email.
Robbinhood Ransomware Hits Two Power Companies in India
The TRU team has also discovered that the Robbinhood ransomware hit power companies in India on April 29, 2019, taking down their company websites, making them inaccessible to utility customers. The power companies were Andhra Pradesh Southern Power Distribution Company Limited, Andhra Pradesh Eastern Power Distribution Company Limited, Telangana Southern Power Distribution Company Limited, and Telangana Northern Power Distribution Company Limited. The ransomware encrypted the companies’ servers, however, the companies stated they had back-ups of the servers.
The power companies are located in the states of Telangana and Andhra in India. It is reported that nearly 400,000 customers visit the company websites each month for information and to pay their utility bills.
Note: The Indian power companies compromised by the Robbinhood Ransomware were both using jQuery, a JavaScript library.
Armor Security Tips for Combating Ransomware
- Do Not Leave RDP Servers Open to the Internet—Many threat actors launching ransomware attacks target “open” Remote Desktop Protocol (RDP) servers as their initial entry into a target’s computer network. The hackers scan the Internet for “open” Internet-facing servers running the RDP service. Once discovered, the attackers will attempt to exploit well-known vulnerabilities in unpatched RDP servers or use a brute-force / password-spray attack at the server (whereby they try logging into the server using common or default usernames such as “administrator” along with multiple commonly-used passwords to gain access). Once the threat actors have accessed the vulnerable RDP system, they simply use it as a steppingstone to the main area of the network and proceed to try and install their ransomware onto target machines in addition to encrypting backups and disabling network protections. Of course, it’s not just RDP these attackers exploit. They also target any service which may grant them access to the core of the network, including JBoss, FTP, etc.
Note: Why do hackers target servers running RDP? Many organizations use RDP instead of a VPN for remote access to their work or home machines. Also, many organizations are not aware the RDP service is running on Internet-facing servers. This could be due to a misconfiguration, a critical oversight in security, or it could be started by another service after the server is deployed.
- Network Segmentation–Implement network segmentation where possible. Having proper network segmentation can limit the blast radius if you experience a compromise.
- Employ strong security controls– Use robust, continuously updated anti-malware and active threat mitigation controls across all endpoint devices and application platforms.
- Keep IT systems and software up to date– Organizations should apply software security patches and updates as soon as possible and often.
- Perform security awareness training–Employees, continually educated about current and emerging cybersecurity risks, can better identify phishing emails and suspicious behavior. Effective awareness training should invoke active employee engagement and institutionalize the correct response to suspected phishing attempts. With proper foundational and enhancement training, employees can effectively act as cybersecurity monitoring and reporting sensors in a potent line of defense against cyber-attacks.
- Backup Storage–Users should have back-ups of their data which is air gapped from the Internet.
- Be smart about passwords: Employees should utilize strong passwords, and NEVER reuse passwords across multiple sites. These passwords should change periodically in accordance with a set policy.
- ALWAYS utilize multi-factor authentication for access to critical systems: This provides an extra layer of security to prevent unauthorized access.
- Develop a secure backup strategy: Ensure all critical data, applications, and application platforms are backed up by password-protected backup/redundancy systems.
- Disable File and Printer Sharing Services, or if these services are required to conduct business, use strong passwords or Active Directory authentication.
- Restrict User Permissions to install and run unwanted software or applications or extensions
- Use caution when opening any attachment even if the sender is known and the file is expected. Watch for unusual or multiple file extensions such as .pdf.exe
- Monitor users’ web browsing habits and restrict access to unfavorable content
- Exercise caution when using removable media such as thumb drives, external drives and CD/DVDs
- Remain situationally aware of the latest cyber threats and trends.