With the cloud, Cloud Security Posture Management (CSPM) tools integrated with other solutions, such as Cloud Workload Protection Platforms (CWPP), have enabled enormous potential for businesses to get security teams closer to global visibility, management, and governance of cyber risk against a master security policy.
This is powerful, as the security industry has struggled to provide a tangible measure of cyber risk across the organization. We also see security and compliance assessments, as well as security capabilities, shift left and extend into the preproduction stages of the DevOps cycle. Due to consolidation of vendor capabilities and features in the cloud security space, the view provided by CSPM and CWPP tools addresses both the “accidental” risk related to misconfigurations, improper settings, and the like, and the “intentional” risk introduced by threat actors and automated threats.
The breadth of visibility provided by the tools across multiple clouds, different types of workloads, and throughout a company’s deployment chain for a broad spectrum of compliance and security controls allows companies to reach security-at-scale like never before.
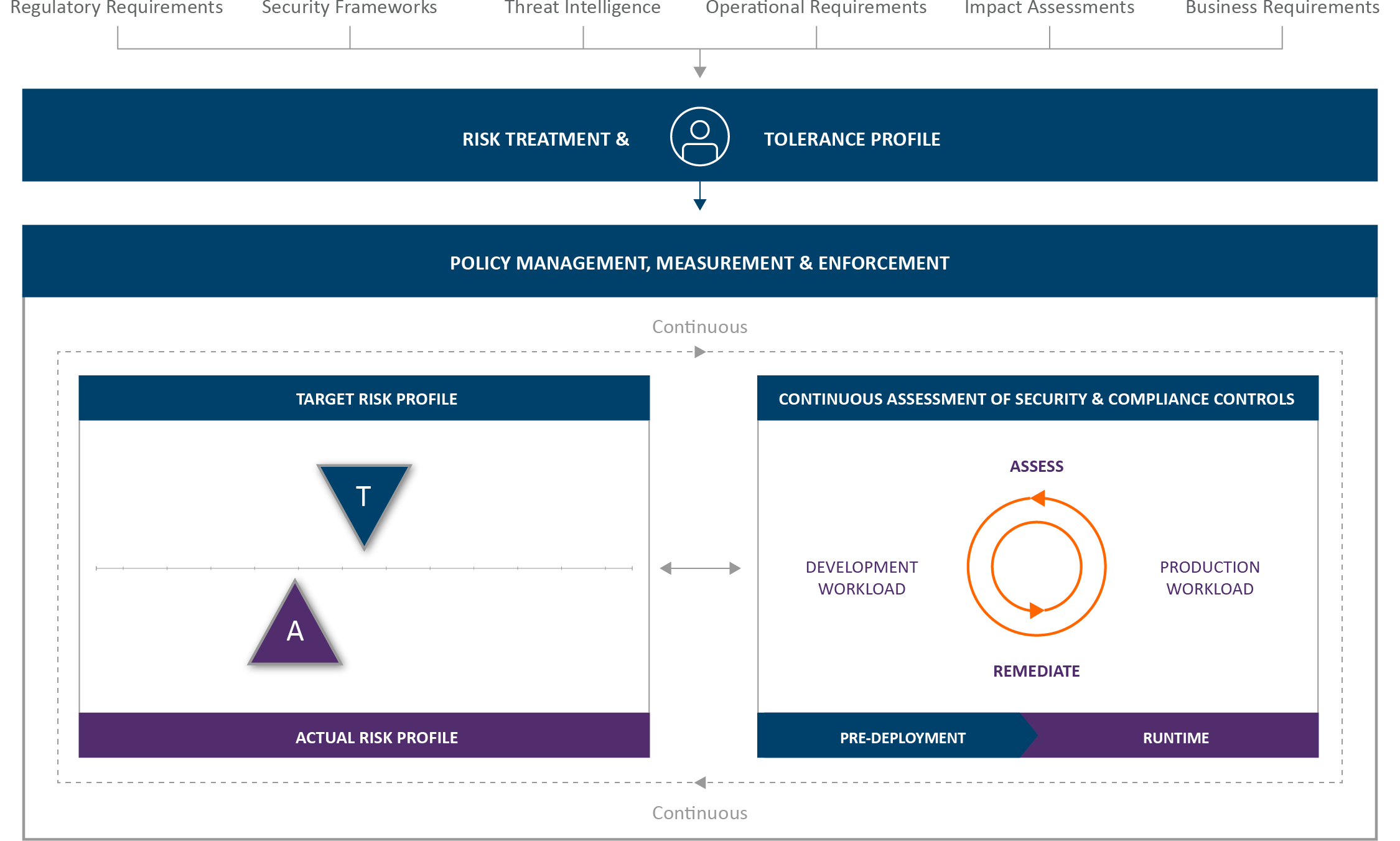
In the graphic below, we see how CSPM tools work at an individual workload level to continuously scan, identify, and even remediate areas of risk based on adherence to a larger security policy in place.
The next graphic provides a global view and reflects the potential for CSPM tools, concerning threat prevention/detection and response capabilities, to become a management, measurement and enforcement mechanism for adherence to a global security policy. In the example, you can see that CSPM tools span hybrid and multi-cloud environments to continuously assess security and compliance controls and practices in place for adherence to security policy. They also provide both alerts for remediation as well as the capability to automate remediation.
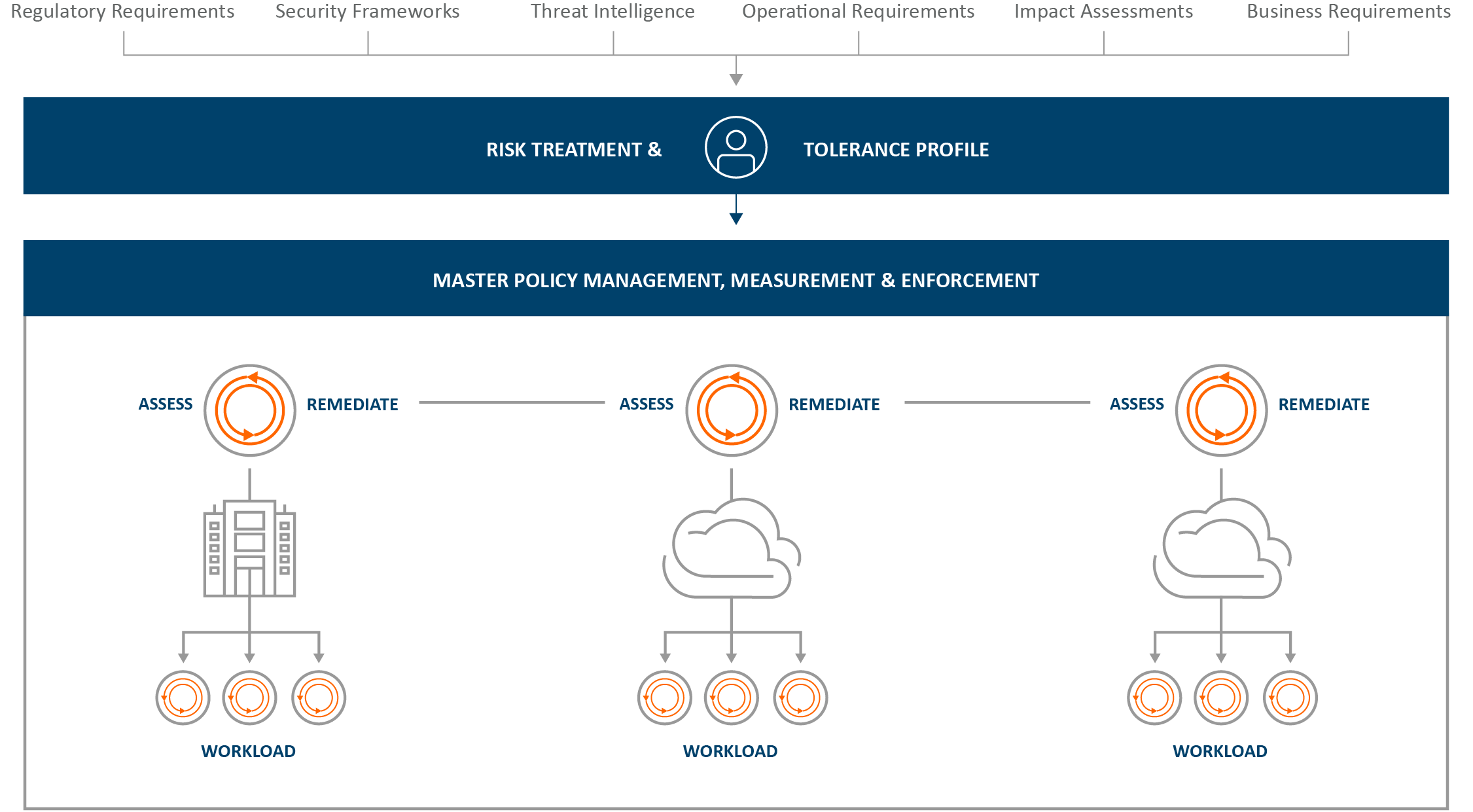
ONE GLOBAL POLICY
This is huge. Managing cyber risk on a global scale through one global security policy means tremendous efficiencies for security, compliance, and secure application development efforts while completely changing the cyber risk equation for businesses.
Establishing Guide Rails Across Teams
Take a smaller enterprise that has as many as 25 different developer teams working on new applications. Today, it’s very difficult for security teams to engage each team and police security and compliance practices across these teams. However, CSPM tools driven by a global security policy can act as an automated mechanism to provide guide rails for these teams. And because the tools are largely automated and can easily inject into the early DevOps cycle, developers are able to seamlessly adhere to policy controls without impacting their ability to produce new code.
Accelerating Secure Application Provisioning
A master security policy can be predicated on pre-formulated templates or scripts, such as AWS CloudFormation templates or Azure Resource Manager templates. The use case here is that various compliance and security profiles can be created for use by IT and DevOps/Developer teams based on the nature of the applications they are currently developing or deploying into production. The templates accelerate secure application provisioning while adhering to overall security and compliance policy.
Mutable vs. Immutable – Wipe and Replace
Cloud capabilities, such as containers and functions, provide organizations with the opportunity to fundamentally change how teams secure applications—to go from “mutable” infrastructure to “immutable” infrastructure.
In an on-premise world, any changes needed to a server (upgrades, fixes, etc.) were done on a server-by-server basis and after that server was already in production. Or, if an infection or worse was suspected, the system would be wiped and reimaged manually, which was always an expensive and tedious proposition. Virtualization and virtual machines certainly made this process much easier and faster and represents an evolution to immutable infrastructure.
However, the cloud allows the opportunity for security teams to fully capitalize on immutable infrastructure.
In this model, production applications cannot be modified. Everything is done with pre-production images. By using containers and image stores, organizations can utilize wipe and replace as an effective security practice that significantly reduces both the probability of a threat actor gaining a foothold into the environment and their being able to stay in that environment long enough to do harm. Combined with orchestration, imagine that any indication that a container may be compromised results in its wiping and replacement with a fresh image. Or, consider automated scheduling that systematically wipes and replaces images for every containerized application every 24 hours. Meanwhile, there is no impact to application performance. You can start to see the advantages to these approaches and understand how the cloud changes the security equation for organizations.
Getting to a Global Security Policy
Getting to the larger security policy is no easy task when considering not one workload, but potentially hundreds or even thousands across multiple clouds as well as your on-premise environments. And those workloads are often spread across business units, developer teams, and even geographies. But your security policy shouldn’t only be about how assets and data are managed below it. Your security policy represents your actual risk management and treatment plan for cyber risk across your organization. That means your organization needs to identify the full spectrum of risk that cyber poses across your organization, and not just in one area.
That means your global security policy looks beyond technology and the current threat landscape to account for the business’ priorities and level of risk aversion. A lot of inputs go into determining an organization’s overall risk profile and appetite for risk. This includes both technical drivers as well as regulatory and business requirements. The idea is to identify and assess areas of potential risk and impact to the business from a cyber standpoint and use that to feed development of your overall security and compliance policy.
Let’s discuss briefly each of the areas security teams and leaders need to assess for risk and gain executive buy-in on risk elimination, treatment, and management:
Regulatory Requirements – What legislative or regulatory framework is your organization subject to, such as PCI DSS, HIPAA/HITRUST, GDPR, or other framework? What operational requirements exist internally for how the business meets compliance with these frameworks?
Security Frameworks – Has your organization implemented or does it follow a security framework such as NIST, CIS, or other framework for how it conducts security across the organization? Have controls and practices been cross-referenced with regulatory requirements to identify overlapping requirements for reconciliation?
Threat Intelligence – What does strategic, generalized threat intelligence suggest as emerging threats your organization should be aware of, and what steps are recommended to counter these threats? What does any specialized (specific to your organization) threat intelligence and operational performance data suggest are areas of risk for treatment and investment? What is the current state of your security posture?
Operational Requirements – Operational requirements are associated with maintaining operational integrity across business systems, production systems, and other key areas for the business from risk of downtime or disruption. Have these been identified, and what tolerance has been assigned to each?
Impact Assessments – Have any risk assessments, whether conducted by internal personnel or by a third party, been performed on the potential impact of a failure in security and compliance controls and processes? If so, what exposures and risk were identified?
Business Requirements – What are the requirements for the business overall that security teams must support, including digital transformation and other strategic initiatives, new business ventures, acquisitions, etc.?
Creating an overall risk profile that feeds into development of your global security policy is no easy task. It is a thoughtful and comprehensive look across the organization for areas where cyber introduces potential risk. And you should expect that your organization’s risk profile and appetite for risk will change over time. However, by working in the cloud and using tools such as Cloud Security Posture Management, security teams and leaders have an opportunity to fundamentally change the game in how cyber risk is managed up and down the business.
For more information on Cloud Security Posture Management tools, see our other posts on this topic.
For information on Armor’s CSPM solution, Automated Security and Compliance – RedLock solution, click here.