When it comes to physical threats, business decision makers and executives are quick to invest in preventative measures that will thwart attacks. Whether it’s putting locks on front doors, storing critical materials in a safe or buying insurance, it’s easy to spend money on asset protection when there’s a tangible threat. When it comes to cyberattacks and protecting digital assets, however, organizations appear more hesitant to invest in proactive security.
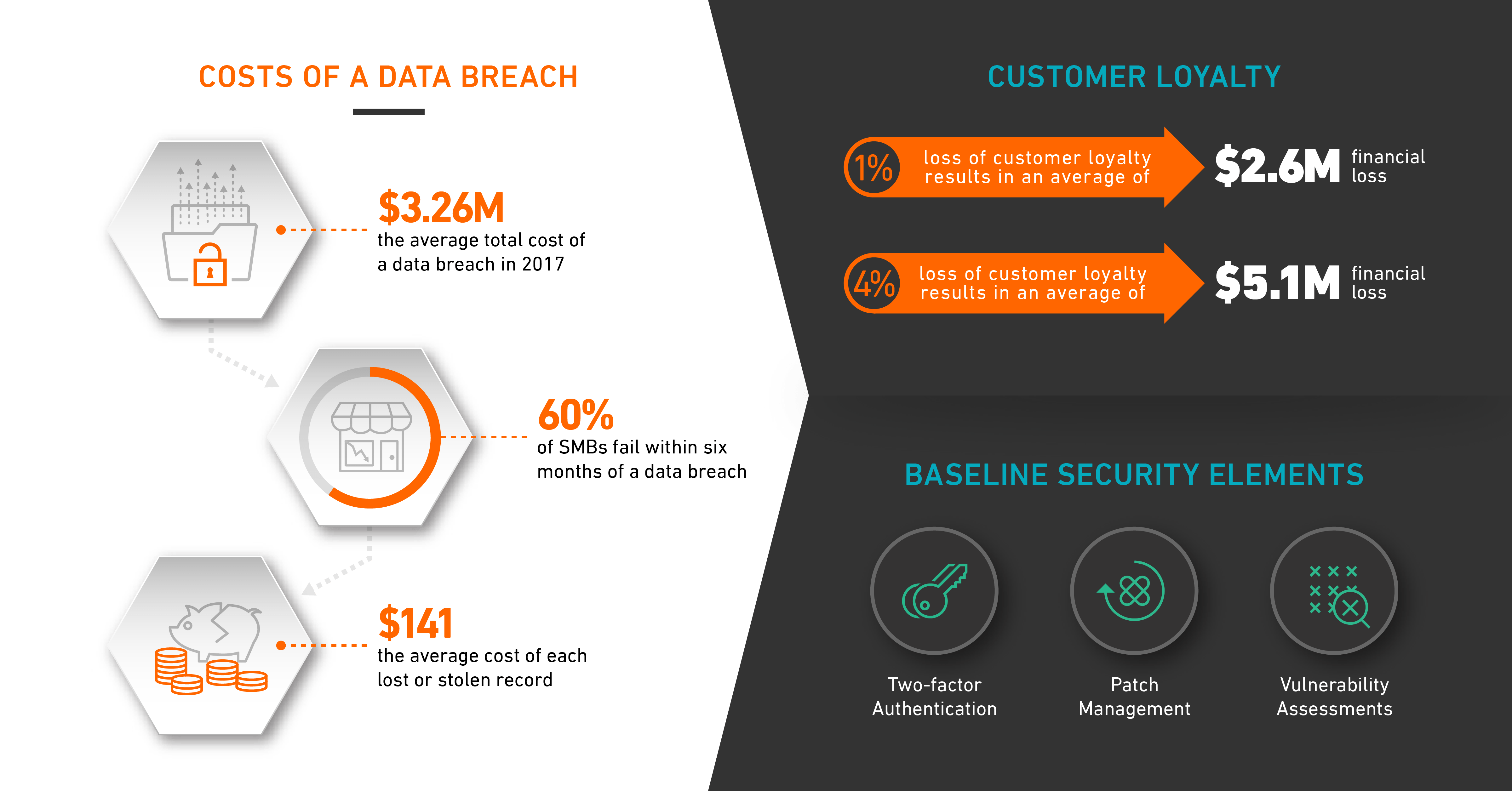
Although the cost of a robust security program and monitoring system, either on-premise or outsourced, can be expensive, it’s typically far cheaper than the aftermath of a data breach. According to Ponemon Institute’s 2017 Cost of Data Breach Study, the average total cost of a data breach in 2017 was $3.26 million. Cyberattacks pose a huge financial threat to businesses every day, and no matter how large or small a company, the reality is that today’s organizations can’t afford an attack.
Recent events show…
One of the largest breaches in history occurred last year when Equifax revealed that the personal information of 143 million customers was exposed. While the exact cost of damages is still unknown, within one week the credit company lost $4 billion in stock market value. This is only one of many examples. Fortunately for large enterprises such as Equifax, Home Depot, Yahoo!, Uber and others, cyberattacks aren’t necessarily business-ending since financial resources and customer loyalty can help sustain companies through the aftermath of a breach. Still, they are catastrophic, and not just for the company’s bottom line or the poor soul at the helm of security, but the executives as well. The CEO of Yahoo lost her 2017 bonus due to the famous breach, Equifax ousted the CIO and CISO following their breach.
Small and mid-sized businesses, on the other hand, typically face more devastating consequences. The National Cybersecurity Alliance has found that 60 percent of small businesses fail within six months of a data breach.
Leading factors of a breach
Two of the primary reasons companies experience data breaches are lax authentication controls and failing to patch their systems.
There are several baseline elements to every security program, and one of the most critical components is user management and authentication controls. Many companies do a poor job of ensuring that the appropriate authentication security controls are set in place for the business, users and administrators. Best practices and industry standards dictate multifactor authentication and administering systems through trusted VPN endpoints. While hackers can infiltrate a system in a variety of ways – brute force, insider misuse, etc., many threat actors gain access to networks due to lax authentication controls, such as weak or reused passwords.
Additionally, patch management is crucial to mitigating the chances of a breach. The majority of present-day breaches are successful because an organization is behind on patching its systems. Attackers still leverage old exploits that target vulnerabilities released years ago because they will still work. Many of the common exploits used today target 2 to 5-year-old vulnerabilities. Often, patching is neglected because of the operational cost associated with testing the patches and ensuring the system works post patch. In some cases, the software is no longer able to function in an environment once patched, so the risk is accepted. If the system has external exposure where no mitigations can be put in place to reduce the risk posed by the vulnerable system, simply accepting the risk should no longer be a viable solution as it changes from an “if” to a “when” the attack will succeed. A solid patch management solution identifies applicable patches, tests them in a cert environment prior to deployment to the production environment, with continual follow on. Patching is not a quarterly ordeal, you must be committed to ensuring your systems are patched and secured.
Vulnerability assessments are an invaluable part of any security program and are used to identify issues that might have been overlooked. They are generally conducted using vulnerability scanners that rely on signatures looking for known vulnerabilities in systems that the scanner can communicate with. The issue comes about when they are not properly employed and are unable to communicate with all devices within the environment. They are often utilized prior to penetration testing to focus the efforts of the tester, setting the stage for a meaningful penetration test that can truly validate the security controls of an organization instead of a mere check in the box that we see all too often. The important point is to validate the security controls you have put into place. These controls are not something companies can just set-and-forget; they need to be constantly validated and reassessed to ensure they adequately protect against applicable attack vectors.
Is the investment worth it?
The cost of a data breach extends far beyond paying industry regulation fines. It also includes factors most companies might not consider, including help desk activities, internal and external communications support, special investigative activities, remediation, legal fees, product discounts and identity protection services, to name just a few. Of all of the aforementioned expenses, perhaps the hardest hit a company can take post-data-breach is the loss of customer trust in your brand.
A recent example of this is the Facebook and Cambridge Analytica privacy scandal. Although there was no breach of user data in this instance, Facebook lost the trust of users worldwide because of the misuse of information. Cyberattacks tarnish an organization’s reputation and perception among customers, and it’s often difficult for businesses to regain that confidence, as consumers no longer trust the organization to responsibly store their information. The 2017 Cost of a Data Breach study notes that companies that lost one percent of their customer base following a data breach experienced an average financial hit of $2.6 million, and those that lost four percent or more suffered an average of $5.1 million drop on their bottom line.
Too often we see companies respond reactively, as opposed to proactively, to a cyberattack by paying fines and investing in security afterward. However, with the average cost of each lost or stolen record containing sensitive and confidential information calculated at $141, according to the Ponemon study, companies large and small can ill-afford to have reactive attitudes toward cybersecurity. Besides, positive press coverage after a data breach is non-existent. The public doesn’t care what companies are doing after their information has been compromised; they need to know what’s being done to prevent that from happening to begin with.
At the end of the day, no one wants to pay the upfront costs for cybersecurity, but without it, the repercussions are unacceptable. Not to mention, there isn’t a security professional out there who wants to be the person who allowed a breach occur. As the average size of a data breach continues to increase (by 1.8 percent in 2017, according to Ponemon Institute), it’s time for companies to learn from others and invest in cybersecurity before they become another statistic.