The amount of data enterprises manage and store continues to explode, and there is no end in sight. Keeping pace with that growth is not easy, especially when it comes to security. Between external attackers, malicious insiders and employee mistakes, data often finds a way of leaking into the public domain. In this climate, encryption is a necessary safeguard for sensitive data – and not only as it moves around the network.
Protecting Data at Rest
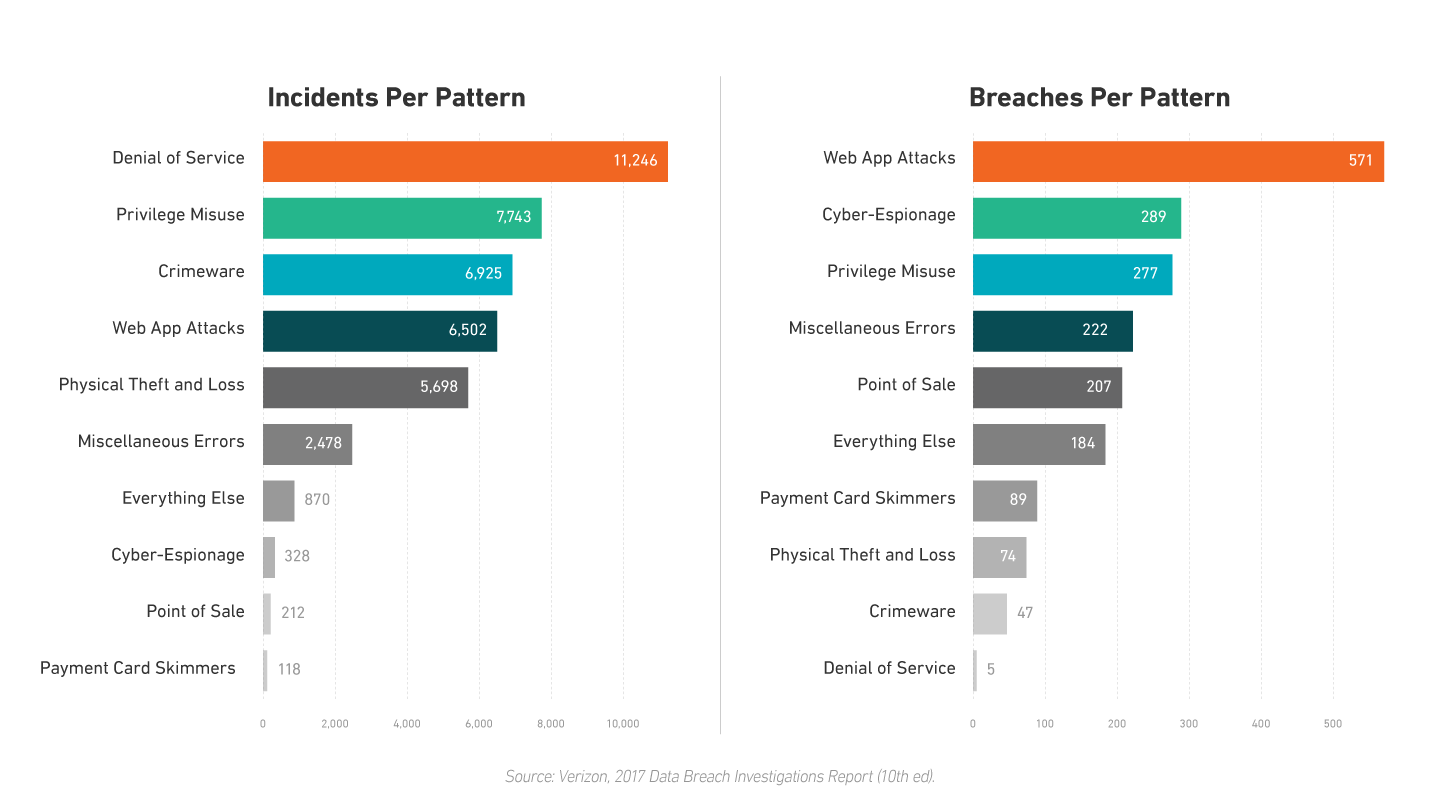
On the surface, inactive data sitting inside a database may seem like less of a target than data in transit. However, examine some of the worst data breaches in recent memory, and it will reveal the opposite is true. According to the Verizon’s 2017 Data Breach Investigations Report, physical loss and theft of devices accounted for nearly 5,700 of the 42,068 investigations, and nearly four percent of those incidents resulted in a breach. While the vast majority of the incidents are not known to have resulted in data disclosure, one point is clear – people lose things, including their devices, and any device without encryption represents a potential data leak.
The distributed nature of today’s workforce also poses a challenge. With remote workers operating in far flung locations, including outside the country, keeping devices loaded with corporate data safe is vital. Encrypting data at rest accomplishes this.
But perhaps most important is the role it plays in preventing data breaches caused by hackers stealing user credentials. According to the Verizon report, 81 percent of the hacking-related breaches leveraged either stolen and/or weak passwords. Data-at-rest encryption, however, can prevent the theft of user credentials stored on the stolen/misplaced device in addition to keeping confidential files secure.
If It’s So Good…
…then why aren’t more companies doing it? Well, the answer is partially about technology, and partially about culture. Some organizations view encryption – and the associated key management issues it creates – as being cumbersome and inconvenient. Depending on how many encryption tools an organization is using, there could be hundreds or even thousands of encryption keys for them to safely store and manage.
Challenging enterprises further is the ad hoc approaches they have taken over the years. Lacking a centralized policy and control of encryption efforts, some organizations have found themselves confounded when dealing with recovery and key management.
It is not uncommon in a large enterprise for fragmentation to take hold, leaving many devices either unencrypted or not encrypted according to the corporate standard that is supposed to be in place. Then there’s the culture barrier. When it comes time to access data, encryption that isn’t transparent to the user can be a turnoff, particularly when end users are accustomed to other encryption tools.
Implement Encryption Successfully
While challenges abound, deciding not to implement data-at-rest encryption is not an option for many businesses. Compliance mandates, such as HIPAA or PCI DSS, create a situation in which failing to protect data at rest can leave enterprises open to penalties and litigation. Even without regulations, leaving data at rest unencrypted can result in a hefty price tag in the form of customer churn and reputation damage if a breach occurs.
Creating an encryption strategy takes collaboration between IT, business unit leaders and operations. It is not just a matter of technology – compliance regulations and business considerations must be accounted for as well. The focus then should be on identifying the data and devices that need to be protected. Another report found that of the roughly 4,800 individuals surveyed 59 percent said discovering where sensitive data resides in the organization is their most difficult challenge. In addition, 36 percent of respondents see classifying what data to encrypt as a significant issue. Data discovery tools can aid this process, but it is also important for stakeholders outside the IT department to guide discussions about what data is critical to operations.
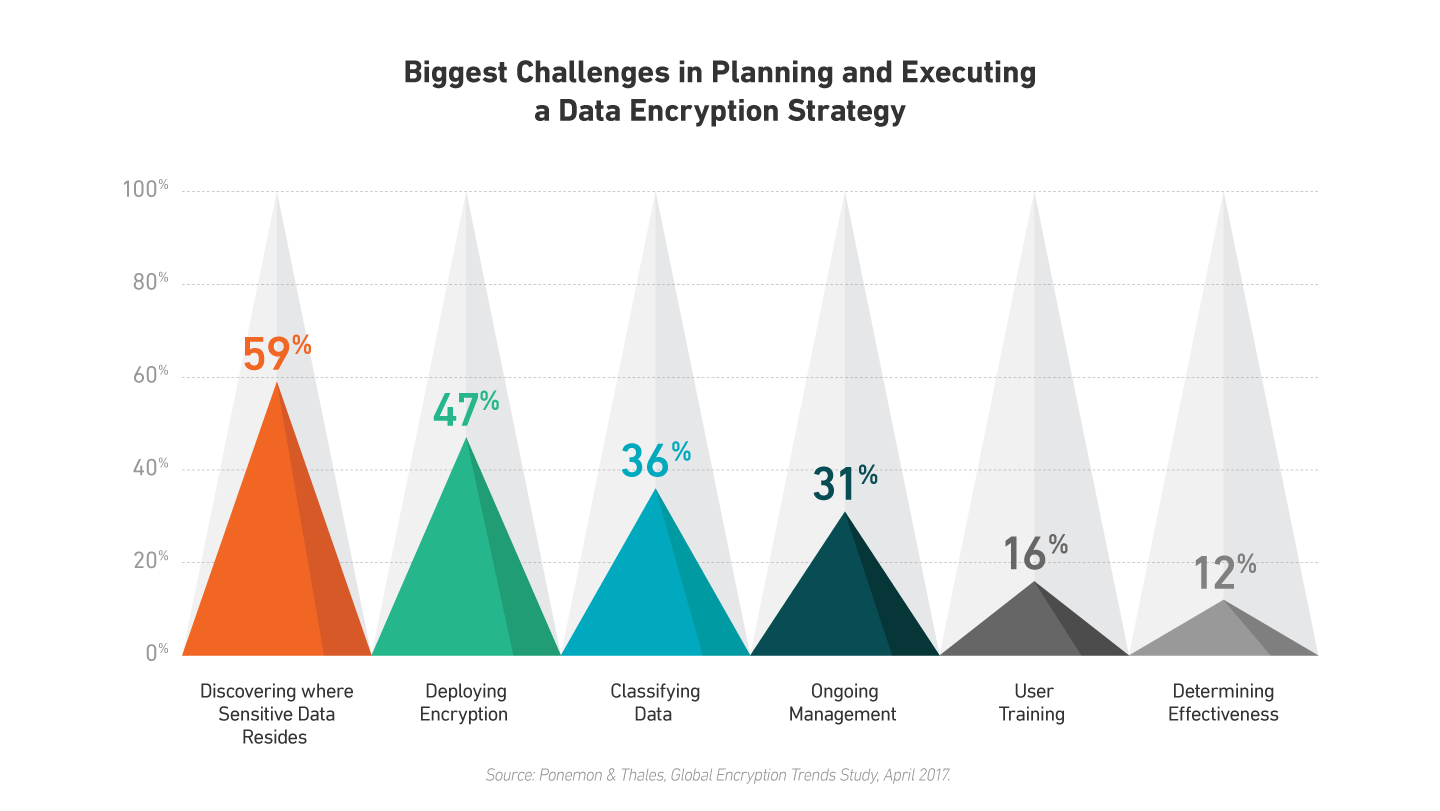
Deciding on a consistent key management strategy is also paramount, as is establishing an encryption policy and giving it teeth. Focus on user education and get feedback, but also take a hardline with violators. Protecting data as it travels is critical, but don’t forget – that same data is just as valuable when it is sitting on a powered-off laptop.
To learn how to protect your data at the network and cloud server levels, read our blog: Keeping Them Out of Your Vault: Network Segmentation in the Cloud.