What if I told you that for as little as $10, I could use your credit card without your knowledge or permission? Thanks to the Dark Web, I can.
From track data dumps to cloned cards, the buyers and sellers on Dark Web forums are in the market for credit card information, and there are several ways for them to get it. 2017 saw several well-publicized data breaches where credit card data was stolen, including breaches at Kmart and Sonic.
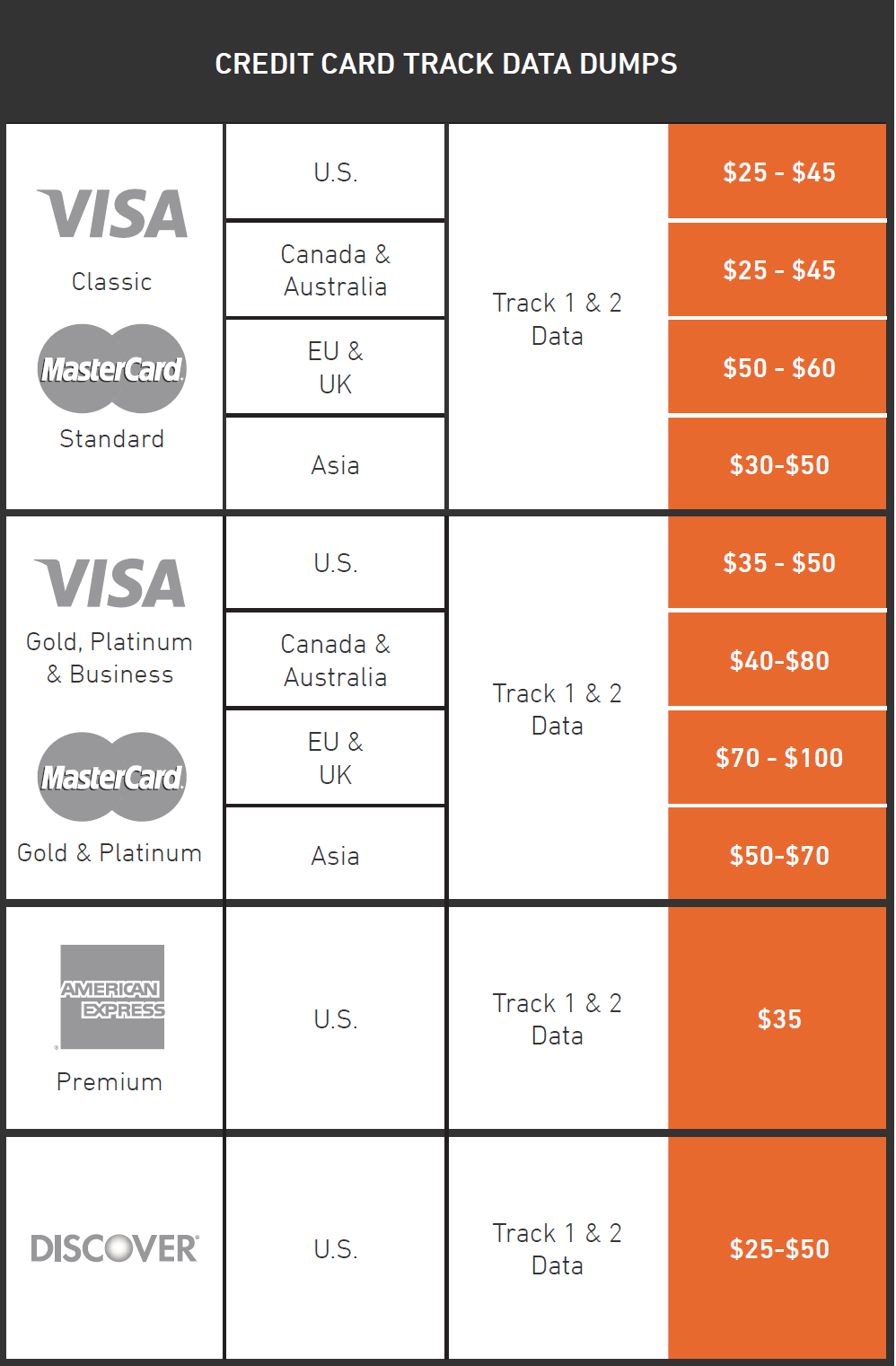
In our new Black Market Report, the Armor Threat Resistance Unit (TRU) researchers uncovered a bustling underground economy where magnetic stripe readers, cloned credit cards and more are all available for the right price. The market for both credit card data and the hardware and malware that make it possible is going strong. Bank webinjects and remote access trojans for example can be purchased for $200 each. A password stealer was being offered for $50. Everything the aspiring scammer needs can be purchased online.

One of the oldest and yet still common ways cybercriminals obtain credit card data is through skimmers. In fact in February, the Dallas police department investigated the presence of half a dozen skimmers placed at gas pumps in the Pleasant Grove neighborhood.
The hardware needed to run a skimming operation is commercially available, though purchasing the equipment legally of course would leave a paper trail. That is part of the beauty of the Dark Web, where identities are masked and purchases are untracked. It is in this underworld that criminals can purchase an ATM skimmer for prices generally ranging from $700 to $1,500. Magnetic stripe reader/writer(s) – which criminals can use to create their own skimmers – are for sale as well, typically costing between $400-$990.
These devices, which can be placed at gas pumps, vending machines and elsewhere, can be very convincing, even mimicking security mechanisms intended to prevent skimming. At the low end, skimmers just record data into onboard storage, which adds the additional risk for the scammers of having to physically or remotely retrieve the data. The more expensive and sophisticated skimmers may connect to an off-site storage location in real-time that the criminal can access without being caught.
Skimmers may be difficult to detect, but there are measures that can be taken to mitigate them. First and foremost, if the credit card reader you are about to use looks oddly bulky, has multiple colors as if it has been repaired, or obviously has additional components sticking to the outside of it, don’t use it. In addition, consumers should be wary of using credit card readers in areas that are unmonitored or easily accessible. While gas pumps and ATMs are usually monitored by attendants and cameras, vending machines for example may be located in dark or awkward-placed hallways.
Cameras however can pose their own problem. Fake cameras can be set up to capture PINs and other information entered at a kiosk. If a camera seems oddly placed, like it isn’t part of the kiosk, or seems focused strictly on the number pad, consider finding a different kiosk. There are also RFID skimmers, which are a whole other class of skimmers, as they allow criminals to scan your credit cards just by getting close to you in public. RFID scanners can be mitigated by carrying your credit cards in RF-shielded sleeves or wallets.
However, skimming devices are only one way for criminals to steal credit card data. Plenty of data theft still goes on via phishing, social engineering and other means. The easiest precaution to take to protect your information online is to only enter credit card information through a browser on a computer and network you trust, as well as to check to make sure the site you are using leverages both encryption and a valid certificate to protect your connection and transactions.
One final step that is often overlooked is monitoring your credit card account for fraudulent activity. While this won’t prevent anyone for stealing your data, is represents your best chance of minimizing damage if they do.
Want to learn more about the cyber underground? Download our Black Market Report: A Look into the Dark Web.