Unlike legitimate cybersecurity jobs, cybercrime does not require certification or advanced degrees. In fact, the barrier of entry into the world of cybercrime remains extremely low, in large part due to the growth of cybercrime-as-a-service on the Dark Web.
In The Black Market Report, our Threat Resistance Unit (TRU) researchers identified a full menu of service offerings that anyone with the time, motivation and a computer can gain access to.
One of the most noteworthy services provided is a distributed denial-of-service attack (DDoS). Designed to make a website or system unavailable by overwhelming it with traffic, DDoS attacks can be very disruptive for businesses and cost significant amounts of money due to downtime.
In January 2018, a New Mexico man admitted in federal court that he hired DDoS services and used them to launch attacks against several websites during a roughly two-year period from around July 2015 to around March 2017. The man, John Kelsey Gammell, confessed to directing DDoS attacks at websites operated by companies he used to work for, competitors of his business and companies that refused to hire him. He also targeted websites for law enforcement agencies, courts and others. In addition to using computers of his own to launch these attacks, he purchased subscriptions to multiple DDoS-for-hire companies, including CStress, vDoS, Inboot and IPStresser.
In our analysis of DDoS offerings, the TRU team found that the prices for DDoS services vary according to multiple factors, including the length and difficulty of the attack. For example, in one case, the price of a DDoS attack was influenced by whether or not the targeted website had DDoS protections or not, with protected sites being more expensive.

In one case, for servers and sites without anti-DDoS protection, the prices were $70 for a day-long attack and $500 for a week. For sites with anti-DDoS protection, the costs were $150 for a day and $800 for a week. Prices for servers under anti-DDoS protection were $300 for a day and $1,200 for a week.
In another case, a 10-minute DDoS attack was being offered $3, and the price for a day-long attack for a site with anti-DDoS protection started at $200. For sites without DDoS protection the price fell to $50 a day.
In addition to retaliatory motives, DDoS attacks can also at times be used to mask other attacks. For example, in 2015, Carphone Warehouse, a mobile phone retailer in the U.K., was hit by hackers who used a DDoS attack as a smokescreen while they accessed the data of millions of customers and 1,000 employees. In January, the Information Commissioner’s Office in the U.K. fined the company £400,000.
Countering DDoS attacks can be difficult because you never know where they will come from or when they will happen. However, there are countermeasures that organizations can implement to significantly mitigate the risk of a DDoS attack, including:
- Subscribe to anti-DDoS services
- Develop and implement a DDoS response plan
- Implement a reverse proxy with DDoS detection
- Subscribe to threat intelligence services that can provide warnings and indications of potential DDoS activities
While potentially less threatening than some other security incidents, DDoS attacks cost time and money, and the relative affordability of DDoS-for-hire services makes them a cost-effective weapon for everyone from rival businesses to disgruntled former employees.
Want to better analyze the ecosystem of the cyber underworld? Download our Black Market Report: A Look into the Dark Web.
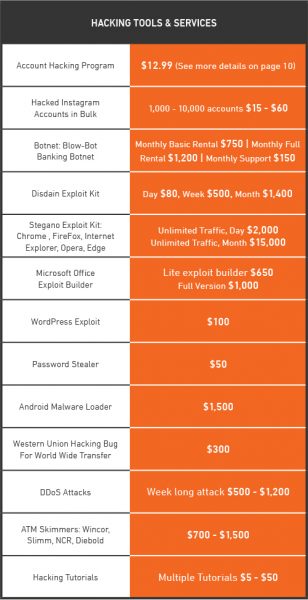
For more information about the available hacking tools, services and associated prices available on the Dark Web, check out our chart below.