How do security professionals know they’re successful in protecting and defending their data? While we rely on several cybersecurity metrics to measure the effectiveness of our efforts, there’s one in particular that many of us here at Armor are passionate about. It’s called dwell time.
What is dwell time and why does it matter?
Dwell time is the duration a threat actor has undetected access in a network until it’s completely removed. Currently measured in days, the average dwell time varies depending on who you ask. Some say the average dwell time is 49 days. Others say it’s even much longer, like 150 days.
While dwell time has been generally declining year over year, it’s still nowhere near acceptable. Mid-level threat actors are attacking vulnerable workloads within minutes and only need 4 to 6 days to infiltrate a network and then less than a day to ultimately carry out their main goal of exfiltrating data.
In fact, the longer it takes for a company to contain an attack, the costlier it will be. This correlation is discussed in Ponemon Institute’s 2017 Cost of Data Breach Study and depicted in the graph below.
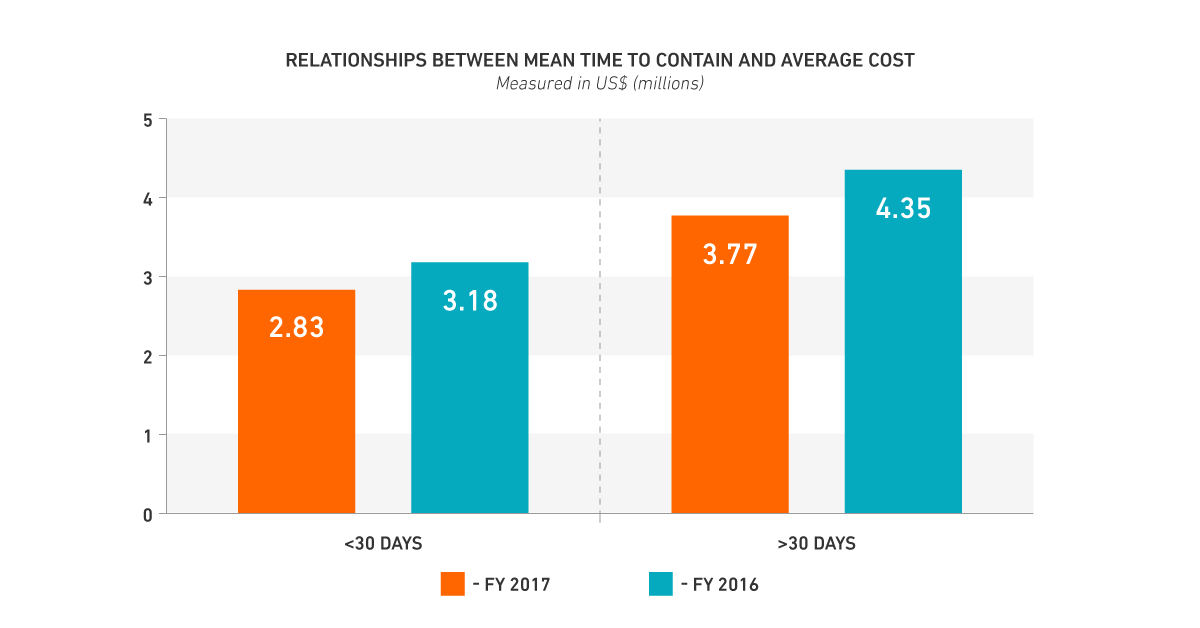
Certain types of malicious software and cyberattacks such as Point-of-Sale malware, banking trojans, and Advanced Persistent Threats require a great deal of dwell time escalate privileges to achieve their objectives (usually to exfiltrate a substantial amount of data). So, if businesses can eliminate the threat at the early stages of the Kill Chain, the resulting damage can be very minimal or even negligible.
Here at Armor, we pride ourselves in establishing a dwell time that is 100x shorter than the industry average. For most cyber criminals, that window of opportunity is just too narrow to complete an attack, and won’t be able to reach the final step in the kill chain, the 7th and last phase (i.e. data exfiltration, data destruction).
So, for businesses, shorter dwell times mean reduced risk of a data breach, a malware outbreak, or their machines getting ensnared in a botnet or held hostage by ransomware. In turn, that would also mean lower chances of downtime, regulatory compliance penalties, and hefty lawsuits stemming from a cyber incident.
How we address and reduce dwell time
We’ve adopted several measures to reduce dwell time for our clients. This includes the following:
1. Leveraging hardened CIS Server builds
We make sure all servers used by our clients are hardened out of the box and adherent to CIS standards. This makes it extremely difficult for threat actors to even initiate a Kill Chain.
2. Implementing an aggressive patching program
Most major malware outbreaks happen because threat actors can exploit vulnerabilities in unpatched software. An aggressive patching program can eliminate known vulnerabilities and thwart the large number of commoditized exploit kits (along with their accompanying malware payloads) that target them.
3. Using on-access scans for anti-malware tools
On-access scans have the advantage of detecting malware infections much earlier than on-demand or scheduled scans by automatically scanning for malware every time a new connection occurs. Previously scheduled scans can leave you vulnerable for the duration of time between each scan.
4. Integrating edge-based traffic shaping
By integrating edge-based traffic shaping, you can prevent known-bad infrastructure from connecting to your infrastructure based on the consensus of the cyber threat research community.
5. Deploying a ‘Zero Trust’ model for server provisioning
A zero-trust model assumes no one (neither outsiders nor authorized end users) can be trusted. As such, we apply rigorous segmentation that prevents threat actors from moving laterally with ease. For example: for websites, we implement a highly segmented multi-tiered architecture. In this case, a web server would be configured to have limited communications with the application server, which in turn would have limited communications with the database server.
6. Using a SIEM that excels at correlating data
Poorly designed Security Information and Event Management systems tend to report thousands of events that are in fact only parts of a handful of events or even just a single event, thereby causing confusion and preventing incident responders from taking the right course of action. We use a SIEM that correlates information exceptionally well and tells us exactly what’s going on. This enables us to quickly analyze an event and respond accordingly.
7. Leverage the Cloud Security Platform
Our cloud security platform combines community-powered insights, advanced analytics, threat intelligence and continuous threat hunting, among other features, to aid members of our SOC in responding and resolving to cyber threats in the shortest time possible.
Dwell time is not the only cyber security metric that we’re focused on. But it’s certainly one that we turn to as a barometer for the efficacy of our operations. For more information on how we work and measure success, visit: https://www.armor.com/how-we-work/.
Learn more about how Armor Anywhere and chat with us if you would like to discuss how Armor can help.