An old proverb states, “the road to hell is paved with good intentions.” We’re willing to bet this proverb wasn’t referring to cybersecurity when it originally came to be. When you think about it, though, it’s highly applicable to one of the biggest threats facing businesses today: insider misuse.
Over-trusting and unaware employees act with the good intentions that, unknowingly can trigger data breaches and deliver enterprise chaos.
Despite an employee’s best intentions to access a VPN, conduct a wire transfer to an individual they believe is a reliable source, or simply open an email – these seemingly mundane actions can have severe and costly consequences. Granted, not all employees are naïve to the fact that they pose a mass threat to their company, and some may even use cyber activities to their own advantage for financial gain, revenge or just plain ol’ bragging rights. However, in cases of insider misuse, we find these cases to be the exception, not the rule.
Understanding insider misuse
Although external attacks tend to make headlines and cause more panic than internal threats do, insider misuse (intentional or not) is still a prevalent issue for organizations around the world.
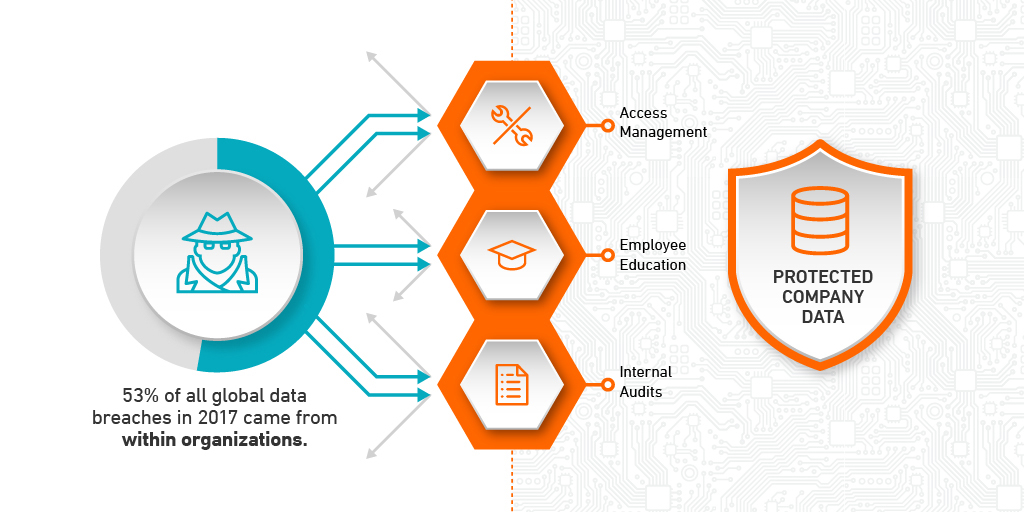
According to Ponemon Institute, in 2017 more than 25 percent of data breaches globally were caused by negligent employees or contractors, while another 28 percent were due to system glitches, including both IT and business process failures. This means 53 percent of all global data breaches last year came from within organizations. More than you thought, right?
Long story short: there’s a huge misconception that nearly all cyber threats come from the outside, which ultimately influences the processes and education that are set in place to mitigate attacks. Thus, businesses spend more time and resources combating outside influences before even considering or investigating internal risks.
A few ways to combat these threats include: access management, employee education and internal audits.
Compliance and internal auditing
While compliance does not equate with security, heavily regulated industries, such as financial technology, government and healthcare, set a benchmark for internal audits – ultimately leading to a stronger security posture. PCI and HIPAA have very strict rules as to who can access what information. There is no need for every employee to have equal access to company data; furthermore, there is strict oversight of those who do have privileged permissions. These guidelines set in place, not only act as a fail-safe for human error, but also keep potentially malicious employees who possibly have too much access from covering their tracks. Although these industries have a leg up compared to the most companies without compliance standards, there’s still a great need for more robust audits to combat internal security threats.
Audits across industries
Ideally, compliance controls would extend into more, if not all, industries to protect all companies’ intellectual property, financial documents and personal data from slipping into the wrong hands. Because not much effort is spent looking internally and auditing user access, time-of-day access and the permissions that certain employees have, most organizations don’t even have the tools to do so. Regardless of the size of a company or type of data collected, oversight controls should be a business standard.
However, until we’re able to achieve this perfect world of security compliance, executives are charged with developing, implementing and demonstrating a plan for protection. To do this, we recommend:
- Keep security and computer-use policies updated
Clearly outline protocols regarding data confidentiality and electronic-media usage.
- Host recurring security-training sessions
Many employees will disregard policies when they don’t understand all that’s at stake. Explain the full spectrum of repercussions that can result from breaking security policies and encourage employees to come forward with any needs.
- Know what tools & applications your employees are using
You can’t fully assess risk if you don’t know the tools your employees are using (e.g., Dropbox and Google Drive) on their company-issued computers.
- Practice vigilant asset management
This sounds like a no-brainer, but it’s a weak spot in many organizations. Always know what you have, where it is, who can access it and how it’s vulnerable.
- Protect yourself against employee risk
Have a system in place to access, audit and review employee systems for updates, and utilize good antivirus software. To mitigate damage from stolen credentials, draft a robust password policy that enforces password resets regularly and prevents password reuse. Finally, filter employee Web traffic through a proxy, so you can monitor and block access to known bad domains.
Reaching employees
Perhaps the largest gap that exists between companies and data security is education. The vast majority of employees should not be expected to understand the breadth of threats facing them daily. Keeping your employees apprised of cybersecurity trends, mitigation tactics, new tools and protocols through ongoing training, company-wide meetings or simple emails will go a long way.
Intentional or not, employees pose an immense risk to the security of your organization. Investing in people and processes to stop these threats before they happen is key to safeguarding critical information that could potentially lead to the demise of your company. And being proactive is significantly cheaper than repairing the damages of a data breach. Make sure those in your organization are doing the best with their good intentions and stop them from lining the path to cybersecurity hell.