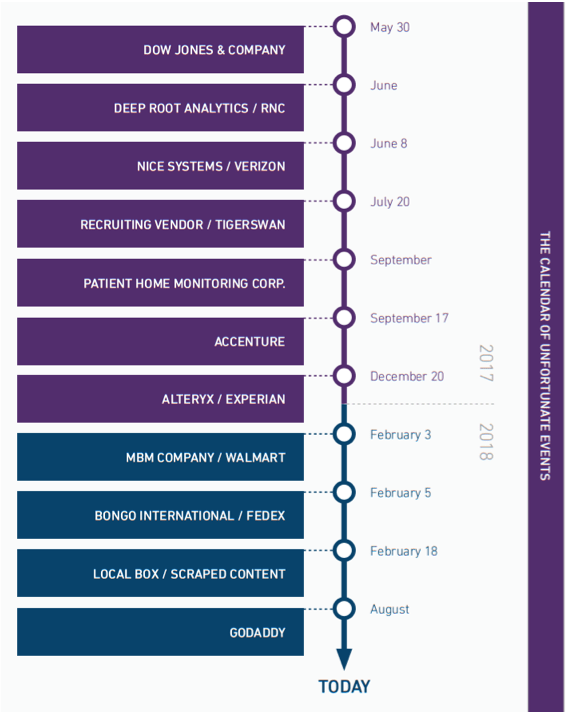
As we continue to discuss Cloud Security Posture Management (CSPM) tools as they evolve in the marketplace and within our own portfolio, it’s also necessary to consider why they’re important. With that in mind, let’s take a look at some context on major data breaches making headlines over the past couple of years, including Dow Jones, Accenture, GoDaddy, and more.
For the sake of this blog, we’ve identified 11 major cyberincidents that involved a cloud misconfiguration and resulted in data exposure. Below are 3 major findings from our analysis:
- More than 386 million records were publicly exposed
- 6 of 11 involved data exposed by an affiliate, partner, subsidiary, or customer of a larger organization
- 100% of incidents involved an exposed AWS S3 bucket
This blog will dive into more detail regarding the second and third findings—third-party risks and exposed AWS S3 buckets.
Third-Party Risk
During our research, we identified 3 major takeaways pertaining to third-party risks in the data. First, these breaches are another example of third parties creating substantial risk for large enterprises. In fact, according to PwC, 68% of the cases where external actors are identified as the main perpetrators of disruptive fraud, those external actors are “frenemies” of the organization—agents, vendors, shared service providers, and customers. Second, it’s clear that the challenge of managing and monitoring third-party risks, especially in the era of the cloud, is still very much a problem. Finally, we actually see where a customer of the larger entity was responsible for the exposure of sensitive data. This last point is interesting and should serve to make security and compliance teams rethink how they manage risks from their customer base vs. just their partners, affiliates, subsidiaries, suppliers, and the like.
AWS S3 Misconfigurations
Each of the data breach examples in the figure above involved a misconfigured S3 bucket. The good news is that this is a relatively simple fix, and most organizations likely have already done so—CSPM tools certainly address this. The bad news is that the 2 firms that discovered all of the aforementioned data exposures appeared to be looking only for S3 bucket exposures at the time. If we could assess whether cloud-based applications were exposed inadvertently, we’d likely see a whole different set of concerns raised. So, in our estimation, the risk of misconfigurations and improper settings of cloud-based applications is likely understated. However, that’s where CSPM tools can provide further value—by identifying and even resolving instances where configurations and settings have made the system vulnerable to hackers.
Armor & CSPM
Armor’s Armor Anywhere and Armor Automated Security and Compliance services together provide holistic security and compliance coverage to address “accidental” and “intentional” cyberrisk. Armor Automated Security and Compliance—RedLock—helps clients identify and resolve misconfiguration mishaps (e.g., leaving cloud storage open to the world, exposing an application to potential exploit by hackers, not enforcing IAM rules, etc.) in security and compliance settings that introduce “accidental” risk. Armor Anywhere provides protection for your cloud workloads from “intentional” attacks by bad actors seeking to steal data.

For more information on CSPM tools and whether you should be considering them, check out our Naked Data whitepaper.