Logging is vital to any cybersecurity program. Combined with proper monitoring, logs can provide valuable information to security professionals that then enable them to detect malware activities, hacking attempts, configuration problems and other similar issues. It’s so important to security – that log management and monitoring are among the requirements of data protection laws and regulations, like HIPAA and PCI DSS.
What is Data Logging Today?
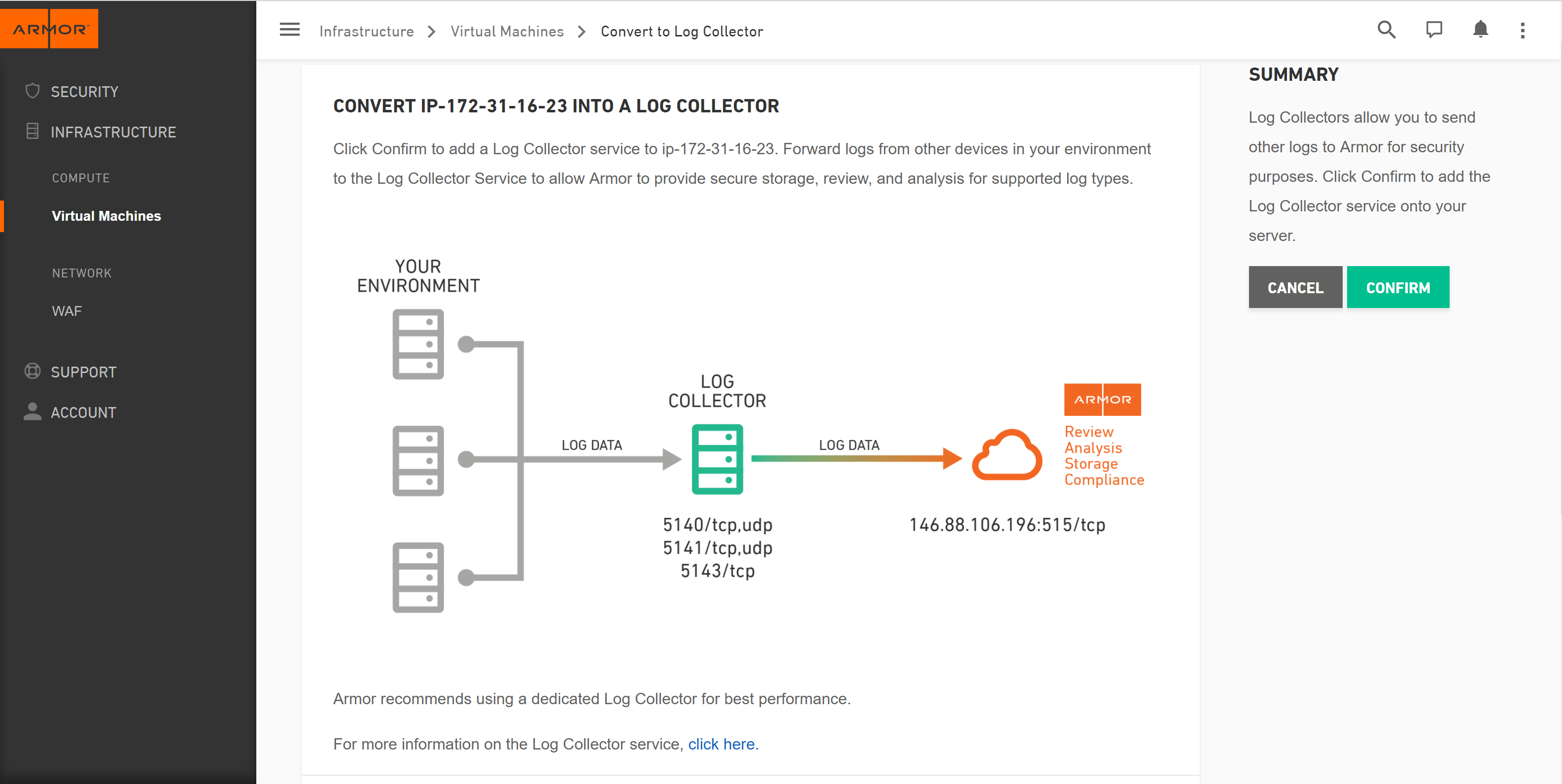
Existing logging solutions in the cloud can be grouped into three buckets: generic log solutions that log everything, those that specialize in security logging, and those that simply provide log storage – all forcing you to review, sort and spend time analyzing data before you can even gain any value from them.
Logging everything
These types of solutions aggregate data from practically all kinds of log sources, including: databases, cloud platforms, operating systems, mobile apps, web servers and many others.
While certainly useful in streamlining the day-to-day operations of your cloud environment, a lot of the information collected by these log systems are not related to security. So, if you need to extract information specifically for security purposes, you will have to filter and decipher the exorbitant amount of unrelated data provided.
Security logging
These are the solutions that log security-specific events. Some of the events recorded by these types of logging systems include account logins, account management, object access, policy changes, system events, and others.
Unfortunately, most of the data recorded by these logging solutions are designed for analysts. So, in order for your organization to make sense of the log data and make security decisions off of them, you’ll need to have someone with the skill to read, parse, interpret, and correlate the data specific to your cloud environments and business objectives.
Log storage
Lastly, there are logging solutions that are simply used for storing log data. The affordability and scalability of cloud storage makes it the perfect place to store a considerable amount of log data over long periods of time – highly valuable for regulatory compliance purposes.
However, cloud storage does not offer any correlative value between logs and some compliance requirements may not be able to be met around speed of retrieving logs. Therefore, security and IT teams are still needed to maintain this cloud logging infrastructure and compliance requirements.
The Future of Logging
But what if security professionals need a logging solution that requires no setup to consume and no effort to gain insight from?
We bring you Armor’s new log management feature. Showcased in our Armor Management Portal alongside the Security Analytics Dashboard, the new feature fills the current gap in existing security logging solutions while adding significant value via actionable intelligence:
- Aligns directly with our Armor Anywhere product offering; meaning, it supports any IT infrastructure no matter the environment type: public, private, on-premise or hybrid.
- Extends security beyond common best practices. More specifically, it’s integrated with our Spartan platform taking advantage of best-of-breed tools and backed by a Security Operations Center (SOC) manned 24/7 by highly experienced security staff.
- Allows you to continue working with your existing technologies, while taking advantage of the skills of Armor’s security experts, who analyze your data and provide a quick report and detailed, downloadable logs – ready for team and company executive conversations. This can be particularly useful for organizations who already have the security tools in place but lack in-house talent to maximize those tools’ capabilities.
Logging for Compliance
The log management doesn’t simply provide logs and analysis, but also stores this data for you with the ability to store logs over extended periods making it ideal for meeting log retention regulatory requirements.
Regulations, like HIPAA and PCI DSS, have certain requirements that specify how long logs should be stored. PCI DSS Requirement 10.7, for instance, stipulates that audit trail history should be retained “for at least one year, with a minimum of three months immediately available for analysis.”
Log retention isn’t the only aspect of regulatory compliance where the log management provides value. Because of our security-first mindset, which goes over and above the minimum level of security typically associated with the checkbox nature of compliance requirements, Armor inherently solves compliance audits and issues.