Misconceptions around cloud migration and security are making it difficult for businesses to complete or even begin their own cloud journey. Unless you’re able to separate the myths from the facts, it will take a while before you can start reaping the rewards of your cloud endeavors, if at all.
The goal of this article is to debunk the major myths that are keeping businesses from realizing the true benefits of cloud technology.
Myth #1: Build the Cloud, then Secure It
As we’ve discussed in detail in the past, cloud security matters. Like in all other areas, cybersecurity needs to be baked into the entire cloud migration and development process. So, when you architect your environment, security should be at the forefront, not a mere afterthought, and a complete understanding of your security posture should be conducted.
In on-premise IT infrastructures, security is predominantly focused on protection against external threats, thus, the implementation of firewalls and other perimeter defenses. But in the cloud, protection needs to be more holistic. Everything adds up to a robust security posture.
In addition to perimeter security, you need to concern yourself with things like application security and how to set up micro-segmentation to counter lateral movement in the network. This is particularly crucial in multi-tenant cloud environments.
If you outsource your cloud migrations, you need to ensure your third-party service providers are knowledgeable of all layers of security required for your specific business-use case. To maximize profits, some third parties provide a one-size-fits-all type of migration and assumes security aspects are the same across every organization, which is simply not true.
Myth #2: Cloud Providers Offer All the Security You Need
This myth has been around since the dawn of cloud computing. Often associated with cloud offerings, where potential customers were told they no longer had to worry about viruses and security patches because the cloud service provider (CSP) took care of these. The misconception is that all security can be entrusted to the CSP.
In reality, all major cloud service providers, (i.e. AWS, Azure, Google) and even smaller CSPs adopt some form of shared responsibility model for cloud security. In which, the providers take charge of securing their facilities, physical network, storage, databases and compute infrastructure. That’s not the entire cloud. You, the customer, will still need to secure the operating systems, virtual network, applications and data.
Securing these assets entails a hefty amount of security responsibilities, including patch monitoring, log/event monitoring, backup/recovery, data encryption, IP reputation management, threat analytics, and many others.
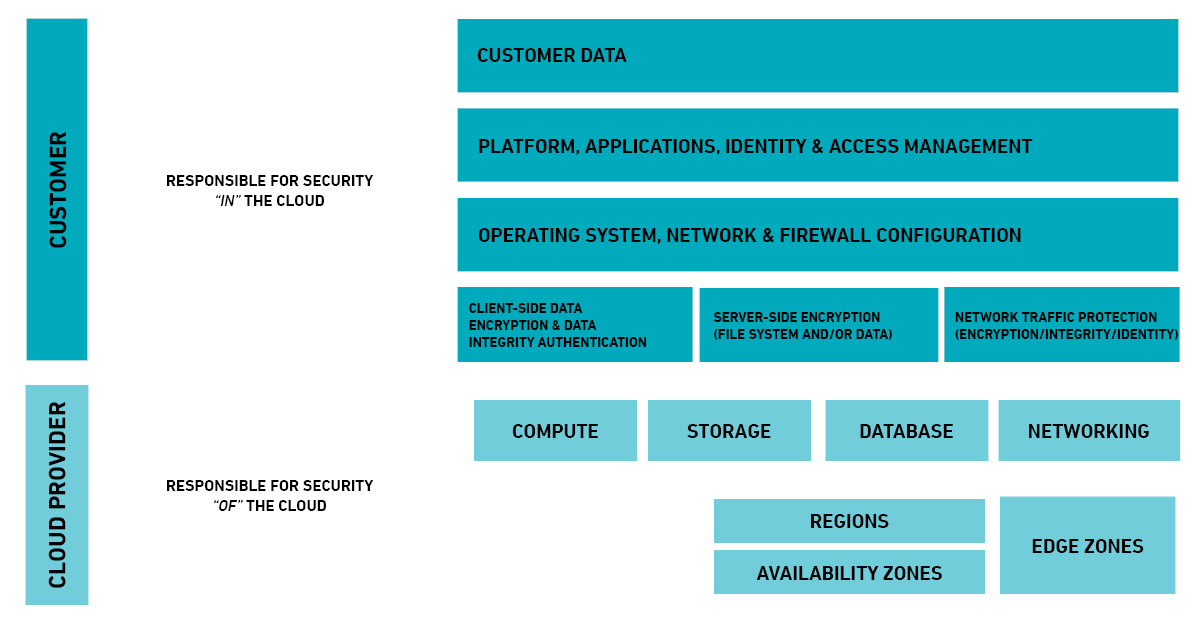
As you can see, cloud customers have a lot of “securing” to do. But that doesn’t mean the cloud is unsafe. That’s another myth by itself. Reputable cloud providers actually provide a comprehensive suite of native controls, which you can take advantage of to secure part of the cloud that you’re responsible for.
Myth #3: Solely Focusing on Cloud & Forgetting Data Strategy
When organizations embark on a cloud migration project, they’re mostly focused on the challenges of moving their data to the cloud. However, they often forget about their holistic data strategy. A poorly configured cloud can expose confidential data to the Internet, as can be seen by several recent high-profile data breaches that occurred due to improper S3 bucket configurations in the AWS cloud. It is important to implement measures such as security group controls, audit trails of IAM activity, and to encrypt data at rest, in-transit and via download.
In addition, you need to be concerned with insider threats and apply strong access controls as well as limit access based on user roles to prevent data leaks due to shared, stolen or leaked passwords.
A common theme underpins these myths. When you separate security from cloud migration, the risk of failing in your cloud journey increases. The temptation to separate them is understandable. The cloud is often perceived as a business enabler, while cybersecurity is often considered an inhibitor. But if you examine them closely, you’ll understand the success of your cloud migration highly depends on how well you’ve incorporated security into it.