Throughout the past several decades, businesses have been influenced and advanced by significant strides made in technology. From streamlined productivity and reduced overhead costs to stronger and more reliable information security, digitalization has been a driving factor of success for companies of all sizes.
In fact, with a steady influx of new technologies that promise substantial benefits, there’s no reason for organizations to not be growing digitally. Executives know that if they refuse to let go of traditional methods, competitors who willingly embrace digital transformation will leave them in the dust.
That said, just because there are many business benefits to digitalization doesn’t mean there won’t be hesitation – especially for those who rely on tried and true methods of documentation, data storage and more. After all, the dangers that accompany digital growth can certainly derail progress, or even put your business at risk. However, fear of the unknown shouldn’t be a reason to stifle growth.
It’s likely that your organization (like many others) started investing in IT years ago and already exchanging and processing documents in digital form. But your digitalization journey shouldn’t end there. The path to digital transformation is never-ending.
Today, one of your many options to gain a competitive advantage is to leverage the stockpile of data you have accumulated in your systems and embark on a big data analytics program. Large enterprises who have invested in big data projects are now obtaining valuable insights that are helping them make informed decisions in business process improvements, marketing, customer service and risk reduction.
Another option is to migrate to a cloud environment, a now common undertaking that has enabled even smaller players to compete with large, monolithic enterprises. Businesses who have undertaken cloud projects have greatly improved collaboration, BC/DR capabilities, availability of services and cash flow, to name a few.
Digitalization, especially when followed with cloud migration, can significantly reduce risk. Unlike hard copies, digitized documents, especially those stored in the cloud, are considerably less vulnerable to fire, flood and other disasters. It’s not all good news, however. While digitalization and technological advancements like cloud computing can reduce one set of risks, they ironically introduce new ones. At the end of the day, business should be focusing on protecting the data as the “network perimeter” has become a thing of the past.
Risks of expanding
One of the first questions companies should be asking themselves when implementing new technologies and being trusted to protect business-critical data is “When should I apply security?” The answer is simple. It’s like building a house; as soon as you’ve got something inside to protect, you put locks on the doors.
So, you’ve already scanned and electronically converted boxes of paper documents and stored the extracted data into more portable hard drives, optical disks and other storage media. Now it’s time to start asking yourself: “What kind of information do I have in those disks?” The volume and type of data you store will dictate the level of risk in your digital environment.
If you happen to have scanned human resource documents, your data will likely include a substantial amount of personally identifiable information (PII). Meaning, you’ll need to implement security measures that would mitigate the risk of a data breach, and, depending on the state you’re in, reduce the chances of incurring penalties from data breach notification laws.
Or, if you’re running a healthcare organization and you’ve digitized copious amounts of medical records, part of that data is going to be electronic protected health information (ePHI). If you store or process ePHI, you’ll have to embark on a tedious HIPAA compliance process and go through an audit that’s just going to wreak havoc in your organization.
The amount of data we store is growing. Last year, the global demand for data storage was estimated to be at 14.8 Zettabytes. That demand is expected to at least double by 2019.
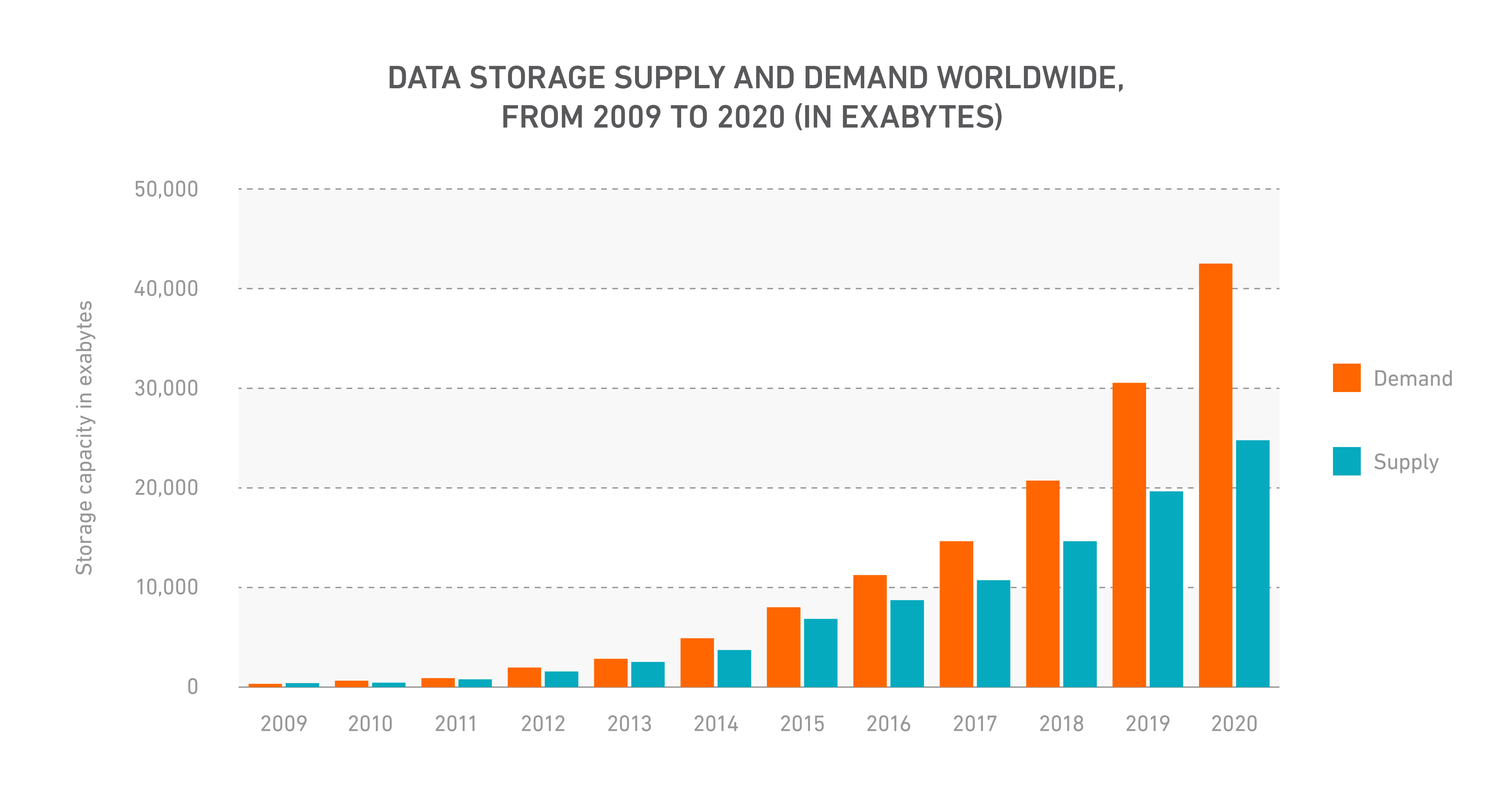
As you add more sensitive information into your digital environment, your level of risk likewise increases since threat actors will have greater incentive to carry out an attack. At the same time, as your digital environment grows, so will its attack surface, and cyber threats will have more entry points and vulnerabilities to exploit.
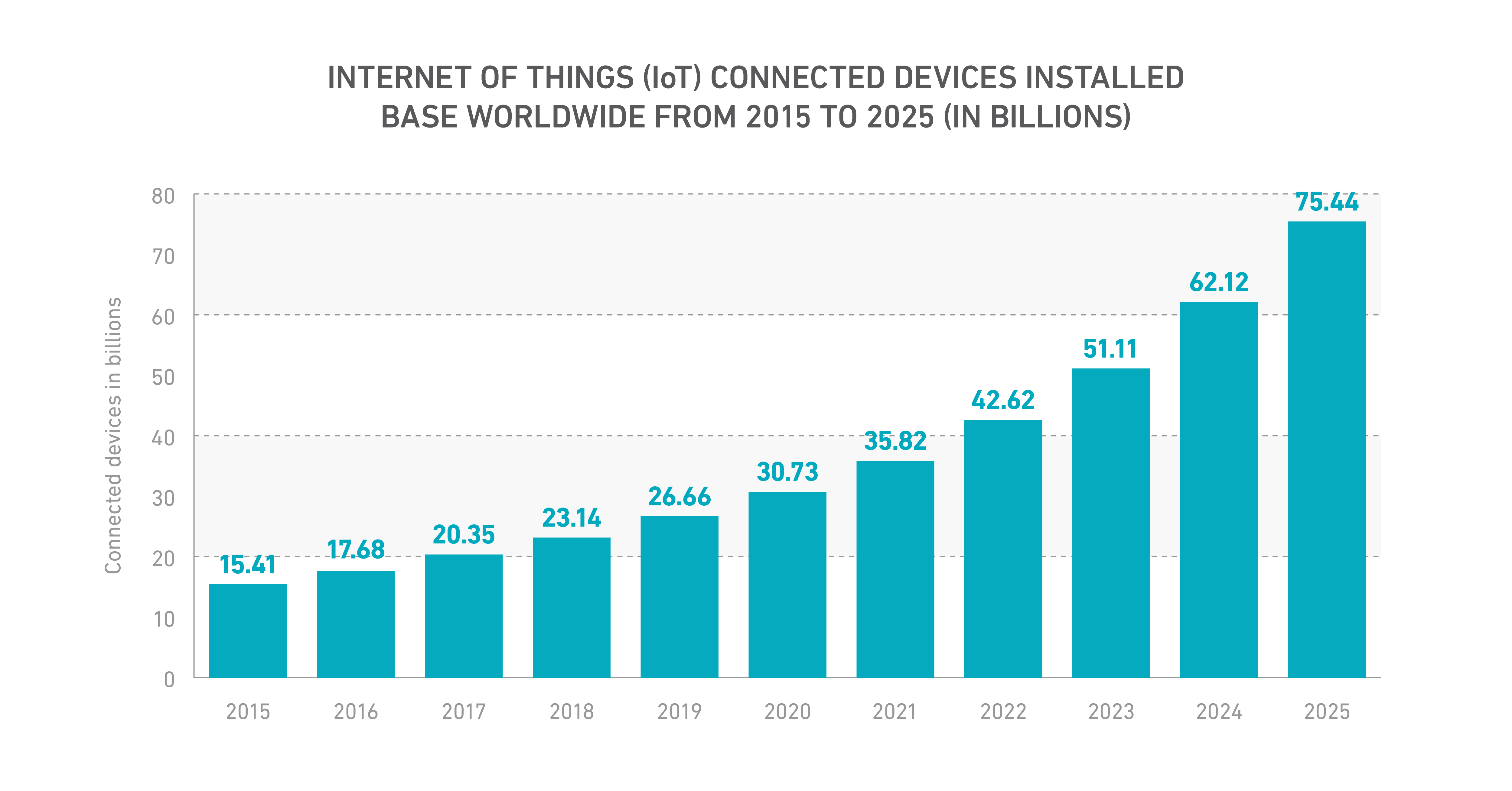
To add to that, consider the increase of IoT devices, which is projected to mushroom from the 20 billion devices in 2017 to over 75 billion devices in 2025. We’ve already seen compromised IoT devices herded into a botnet and used to launch some of the largest DDoS attacks in history. So make no mistake, the threat is real. Just as companies should be growing digitally, they need to grow securely.
Creative security
Because companies have no choice but to embrace digital growth (or risk losing to competitors), they need to be ready for the dangers and challenges that come with it. That means investing in cybersecurity and preparing for regulatory compliance.
While a regulatory compliance undertaking can be very expensive, not to mention extremely disruptive to business operations, you can minimize the scope of what needs to be audited and bring down extra costs and disruptions.
For example, if you must comply with PCI DSS regulations, you can reduce the scope of PCI DSS requirements if you can somehow shrink your cardholder data environment (CDE). Because your CDE consists of the people, processes and technologies that store, process, or transmit cardholder data, one way to reduce your CDE is by removing cardholder data from your systems. But wait, how do you do that if your business processes and transactions also rely on the presence of cardholder data?
Where there’s a will, there’s a way. One way organizations are becoming increasingly clever in the way they minimize the amount of critical data they store is through tokenization. In a nutshell, tokenization substitutes certain types of data (in this case cardholder data) with random values, or “tokens,” and stores the data elsewhere. The tokens can then be used in processes and transactions in lieu of the actual cardholder information.
Because cardholder data is no longer stored in your network, your CDE is reduced, which in turn minimizes the scope of your PCI DSS requirements. In addition, the absence of cardholder data in your systems also lessens your chances of a data breach since there’s no actual data to steal.
One of Armor’s partners, TokenEx, provides tokenization services to enterprises looking to reduce the presence of sensitive data on their premises. Understanding the burden of maintaining compliance and thwarting cyberattacks, the company embarked on a journey less than a decade ago to bring organizations a solution to reduce risks and meet regulatory standards. But if TokenEX is taking in all the sensitive data from different organizations, wouldn’t threat actors now be aiming their sights on them?
That’s right. That’s why these service providers have to really bolster their defenses. In the case of TokenEx, they outsource the security of their cloud infrastructure to Armor to establish itself as a safe haven for sensitive data. In doing so, they are able to sustain their rapid digital growth while keeping risks manageable.
The idea here is, if you want to grow digitally, you should secure what you can and outsource what you can’t. If security is not one of your core competencies, it would be much safer and more practical to entrust the responsibility of securing your digital assets to people who have the infrastructure and expertise to do so.
Check out a couple of additional resources to evaluate your security posture and continue your digital growth: