Another day, another threat. Largely impacting Russian and Ukrainian corporate networks, Bad Rabbit is the latest ransomware to dominate news cycles. While not as widespread or pernicious as its cousins, WannaCry and Petya, Bad Rabbit has the potential to impact systems globally.
How Bad Rabbit Spreads:
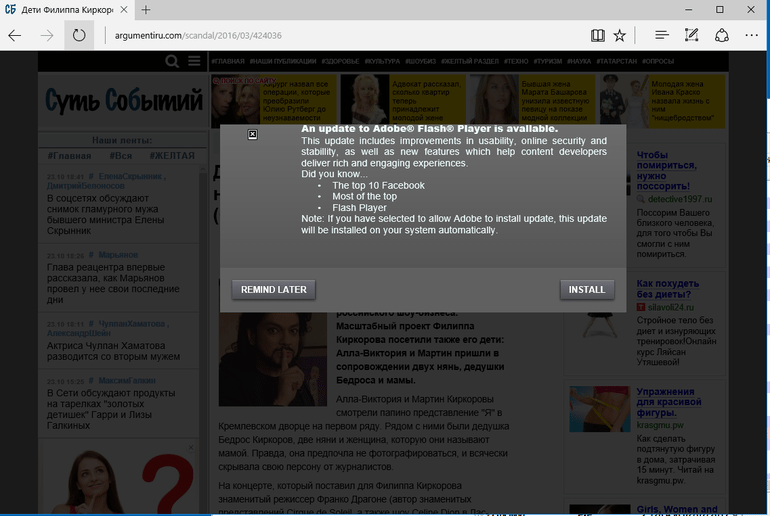
Bad Rabbit primarily spreads through compromised websites known as watering holes. These hacked websites feature a pop-up window (below) that tells visitors that they need to update Adobe Flash Player.
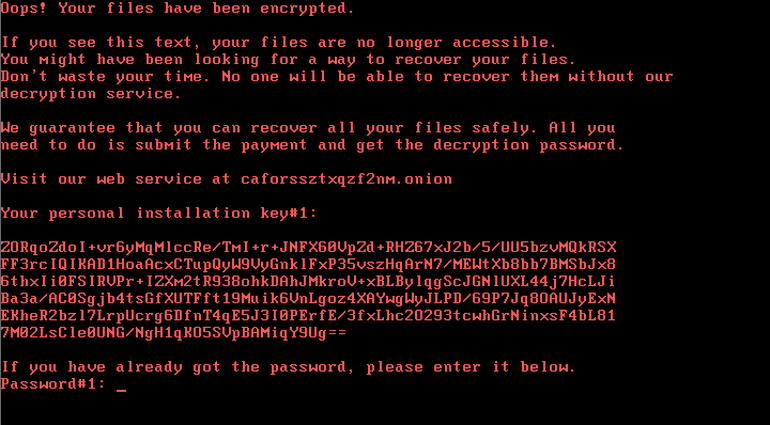
However, this update message is fake and clicking either option, “Remind Later” or “Install,” launches the malware installer. From there, the malware has been shown to spread system-wide from the initial point of compromise, encrypting files and demanding a ransom to unlock them (below).
At this time, it’s unclear if this rapid ability to spread systemwide is due to the use of tools like EternalBlue or just the result of poor password hygiene in the affected systems.
How to Protect Yourself From Bad Rabbit:
While most reported cases are in Russia and Ukraine, there is the potential for this malware to spread globally. Early indications highlight the ability of most antivirus software to detect and block Bad Rabbit.
- Update and Activate Your Antivirus: Early indications show that most antivirus software can detect and block Bad Rabbit. Ensuring that your antivirus is updated and active is a must.
- Avoid Clicking Suspicious Links: Don’t click on any requests to update Adobe Flash Player pop-up. The malware spreads through compromised websites via a fake pop-up window. Clicking either option on the fake installer, “Remind Later” or “Install” will launch the program.
________________________________________________________________________________________________
Images attributed to ESET