At Armor, we interpret the term ‘dwell time’ to mean the duration a threat is present on a protected system until it has been remediated. However, several security service providers (This generically covers managed security services providers (MSSP), managed detection and response (MDR), and security as a service (SECaaS)) have viewed dwell time in a more narrow way.
How other providers have traditionally viewed dwell time:
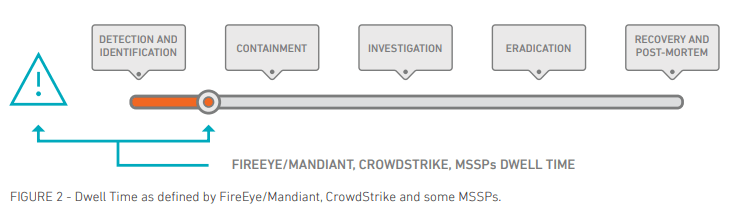
How we view dwell time:
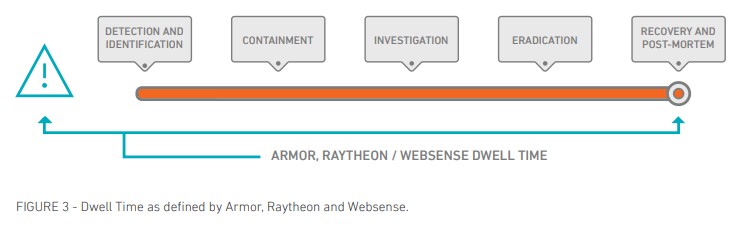
For a more thorough discussion on these two views, alignment of dwell time to the cyber kill chain, as well as dwell time’s implications on security programs is covered in the eBook, “5 Days to Actions and Objective – Dwell Time as a Critical Security Success Metric.” In this blog, we discuss how the traditional view of dwell time came to fruition, the role of MSSPs in shaping this view and its related consequences.
How we got here
In the early days of cybersecurity, organizations placed great emphasis and trust – helped along by the security industry – in prevention and detection controls. During those times, security teams didn’t have effective response functions or experienced response personnel in place because organizations tended to believe that a breach would never happen to them. Prevention and detection were considered the best way to avoid any kind of cyberattack.
Security teams found it sufficient to judge the success of their security programs based on their prevention and detection controls alone. Organizations disregarded the possibility that certain threats might be capable of evading those controls, and therefore, often overlooked the immaturity of their response capabilities.
Gravitation to this narrower definition of dwell time occurred due to its perfect alignment to 1) their perception of the likelihood of a breach happening to their organization and 2) their limitations in cybersecurity, especially with incident response.
As the number of major breaches piled up in news headlines, cybersecurity teams began to shift their thinking to, “it’s not a matter of if, but when we will suffer a breach” – a reflection on the new realities of the threat landscape. It was only after seeing threats strike closer to home that personnel started to look at response in more earnest.
Meanwhile, a similar behavior permeated among MSSPs. Their operations were also at first predicated on a focus of prevention and detection. But as they too started witnessing breaches in the news, they realized an opportunity to develop incident response (IR) practices as premium offerings. These practices were usually standalone or siloed from the managed security side of the house, with only a thin connection to their security operations centers (SOCs).
At the same time, IR pure-plays had practices predicated on response with no visibility into initial intrusion to detection. As a result, these disjointed/siloed operations also lent more support to the narrower definition of dwell time.
It should be noted that, since a threat actor has no idea whether or not they’ve been spotted, detection is not the end of their efforts. Once a threat actor loses access to a machine, they will verify if they still have footing within the target environment as they attempt to regain access. This indicates that the broader definition of dwell time more realistically captures the actor’s full cycle, and proves that syncing response to detection is key – especially in an active compromise.
Both proactive practices, like detection/identification, and reactive practices, like incident response/containment, are crucial in minimizing the cost of a data breach – as demonstrated in the graph below.
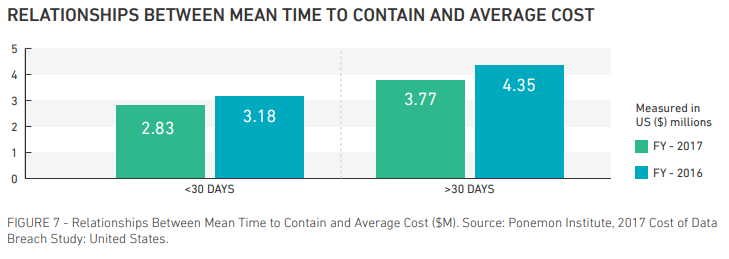
Too Much Alerting and Not Enough Responding
Today, the disconnect between prevention, detection and IR operations is still prevalent among MSSPs and their customers. This, in turn, is adversely affecting overall security. MSSPs and other managed services providers who consider the generation of an alert as the official line of demarcation for their role and responsibilities, just delegate incident response responsibilities to the customer. Unfortunately, organizations are incapable of addressing the many alerts they receive from their MSSPs in the first place.
According to ESG Research, 67% of enterprises receive 5,000+ alerts (all of which require review and handling) per month. However, 42% of enterprise security staff indicated they ignore a “significant” number of alerts because they just couldn’t keep up with the volume. Another 42% indicated they ignore a “marginal” number of alerts for the same reason.
Given the challenges in finding, hiring and retaining qualified security staff, it’s clear that security teams are buckling under the pressure of an onslaught of alerts. More often than not, companies that provide security simply forward a deluge of alerts onto customers as opposed to filtering the information down to address the issues that affect the business. Small businesses and midsized organizations (SMBs), who run with significantly less budget and resources than enterprises, need MSSPs to address the problem in alert management through a more comprehensive approach to cybersecurity that goes beyond alerting to include response with dwell time as a fundamental operating tenet.
Minding the gap
When managed operations only include detection and identification or provide IR as a standalone offering – a common model adopted by most MSSPs today – they introduce a significant gap that further increases dwell time. This gap, which is a consequence of the time consuming, but unavoidable, contracting and legal process, can add crucial hours and days to dwell time.
It’s a proactive security philosophy and culture that drives unified change across all security operations to achieve a common objective – Minimize the opportunity a threat actor has to cause harm to your organization. If you use a managed service provider, it’s imperative you ask them about these same areas and their commitment to and reporting on reducing dwell time.
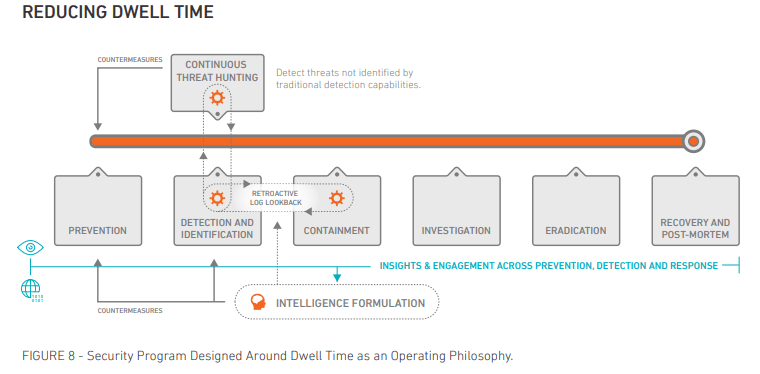
To eliminate these delays, advanced SECaaS providers combine preventive and reactive measures to minimize the chances of a threat actor inflicting significant damage to an organization. Some of the things Armor does in this regard include:
- Leverage hardened CIS server builds
- Implement an aggressive patching program
- Use on-access scans for anti-malware tools
- Integrate edge-based traffic shaping
- Deploy a ‘zero trust’ model for server positioning
- Integrate threat intelligence
- Use advanced analytics and correlations
- Leverage orchestration and automation
- Perform continuous threat hunting
To learn more about these recommendations, download the full eBook: “5 Days to Actions and Objective – Dwell Time as a Critical Security Success Metric.”