With all of the advantages cloud providers offer – convenience, flexibility, ROI – it’s often difficult to resist. Indeed, the benefits are so alluring that corporate managers often buy into security pitches that promise more than can be delivered.
This problem is aggravated by two facts:
- Cloud services are often purchased by line-of-business (LOB) managers sometimes bypassing standard security policies. These managers can be too eager to sidestep corporate IT governance rules and requirements.
- Many cloud vendor security and compliance promises only apply to the layers they directly control, leaving the customer in charge of significant security features that typically go unaddressed. Often, this is due to unawareness of the right questions to ask, and the vendor not providing information that the customer doesn’t want to hear.
However, one of the main ways cloud providers provide value is the ability to scale infrastructure resources as customers’ ] needs change. Indeed, that flexibility along with the speed of how quickly customers can react is a primary attraction to the cloud. And, traditional security models aren’t suited to seamlessly co-exist in this dynamic environment.
Cloud-First Aspirations
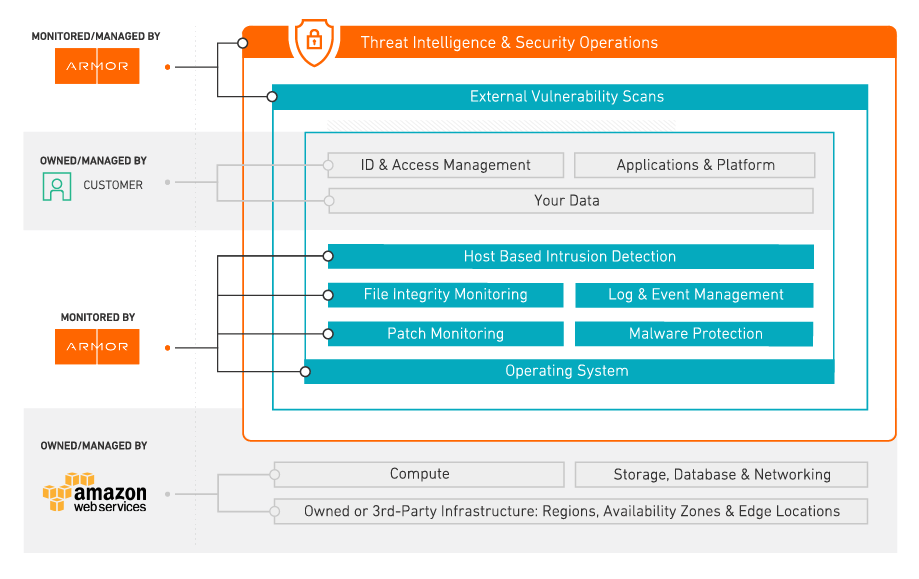
The critical point when thinking about cloud security is that vendors only handle a small portion of the security stack that includes the data center, physical servers and cloud management platforms. The most sensitive elements, including operating systems, applications and data, are still solely under customer control.
This manifests itself in several ways. Consider rules such as PCI for payments or HIPAA for healthcare data. When a cloud vendor claims to be PCI compliant, it is meant literally. In other words, the cloud vendor is PCI compliant, not the companies who are coming along for the “ride.”
Candidly, it doesn’t do a lot of good knowing that the physical server farm or the data center is compliant. For both PCI and HIPAA, all that matters is how sensitive data is managed, and, that data is entirely the user’s responsibility. Monitoring virtual servers against intrusions, monitoring the logs and applying sound security practices against critical data breaches is all up to you. This shared responsibility model is the essence of proper cloud security.
Armor Anywhere’s Shared Responsibility Matrix
Shifting Paradigms
So, how should a company morph its security capability into this elastic business and technology model? Consider that the mechanics behind spinning up a server while bringing another one down can mimic an outage inflicted by a threat actor. At least that’s how it’ll look to the monitoring dashboard.
what should your action be if an intrusion on one of the web servers is detected? Could the answer simply be to power down the VM and allow auto-scaling to spin up a new clean VM?
It’s not merely a matter of changing settings but an entirely different way to operate your security. A team needs to be able to differentiate between a scaling event versus a threat actor. New paradigms in security management must be adopted that harnesses the speed of cloud while effectively defending against threats.
Enterprises must also integrate cloud convenience into their existing security processes. This is far easier to do if you’re partnering with a cloud company that already has a security services focus as its primary business.
That creates the need for a cloud-aware security service that supports your agility needs while providing protection against major cyber threats. At Armor, our customers can easily deploy our agent-based technology to their cloud environments, which subscribes them to our cloud-based security service in the backend. Our cyber security experts constantly monitor customer environments and leverage threat intelligence feeds to protect against threat actors.
Cloud security doesn’t have to be an oxymoron, but it does mean that you have to think differently and partner intelligently.
Learn how to secure AWS with Armor Anywhere
Download the white paper