Pinterest, HGTV, and easy-to-follow YouTube videos have made do-it-yourself (DIY) projects increasingly popular over the past several years. While we all like to think of ourselves as capable DYI-ers, should the security of your organization really be something you entrust to anyone other than an experienced professional?
While there’s no silver bullet when it comes to cybersecurity, most companies recognize the need for a full-time security operations center (SOC). The trouble is, they usually don’t comprehend the resources and time required to manage one in-house.
The call for an effective SOC strategy
The possibility of a data breach is a daily reality for organizations of every size. And while employees clock in and out, threat actors rarely do, making the need for 24/7 protection and monitoring from an SOC even more imperative.
According to Gartner, a SOC is defined both as a team (often operating in shifts around the clock) and a facility dedicated to preventing, detecting, assessing and responding to cybersecurity threats and incidents, as well as assessing and fulfilling regulatory compliance mandates.
A truly effective SOC puts its technology, expert warriors and their actionable threat intelligence to work to protect data assets (whether they’re in the cloud or on-premise) to support business objectives. Doing so requires that the SOC regularly aggregate, normalize, correlate, prioritize and remediate security events.
Large enterprises typically implement a Security Incident Event Management (SIEM) solution, which – although labor intensive and costly – is required for a complete analysis of individual items and events, and to identify connections between a myriad of devices and applications. This allows analysts to confirm whether a security alert is an actual threat or just an anomaly very quickly. If an anomaly, SIEM technology also allows that information to be fed back into the system to make it smarter.
As one might imagine, this process can be lengthy, stress resources and require the ongoing attention of security experts to pay constant attention to its input and output; otherwise, the environment can easily become compromised.
To build or to buy?
In-house
Like many DIY projects, having an in-house SOC might seem like a simpler and more cost-effective solution. While true for most projects, building a SOC requires a vast amount of skill, knowledge and resources. Organizations need to hire, train and maintain enough staff members to continuously monitor and analyze alerts as well as remediate threats. These experts must continually attend internal and external training courses to remain up-to-date on the latest types of threats and methods of prevention, especially since they don’t always have a holistic view of the threat landscape. As the arsenal of cyber threats continues to expand and grow increasingly complex, SOC managers are also challenged with an ongoing search for knowledgeable talent.
Outsourcing
Outsourced SOCs are fully staffed 24/7 with highly experienced personnel who manage the SOC’s unique platforms and remediation tools. Once a threat is witnessed in one environment, the SOC creates and implements countermeasures to protect all of its customers. Quick remediation is paramount to minimizing risk and financial loss, but few companies have security experts in-house equipped to remediate threats in all types of environments. By the time an in-house SOC notices a threat for the first time, in many instances a global, outsourced SOC has not only seen it, but has also created a countermeasure to block it.
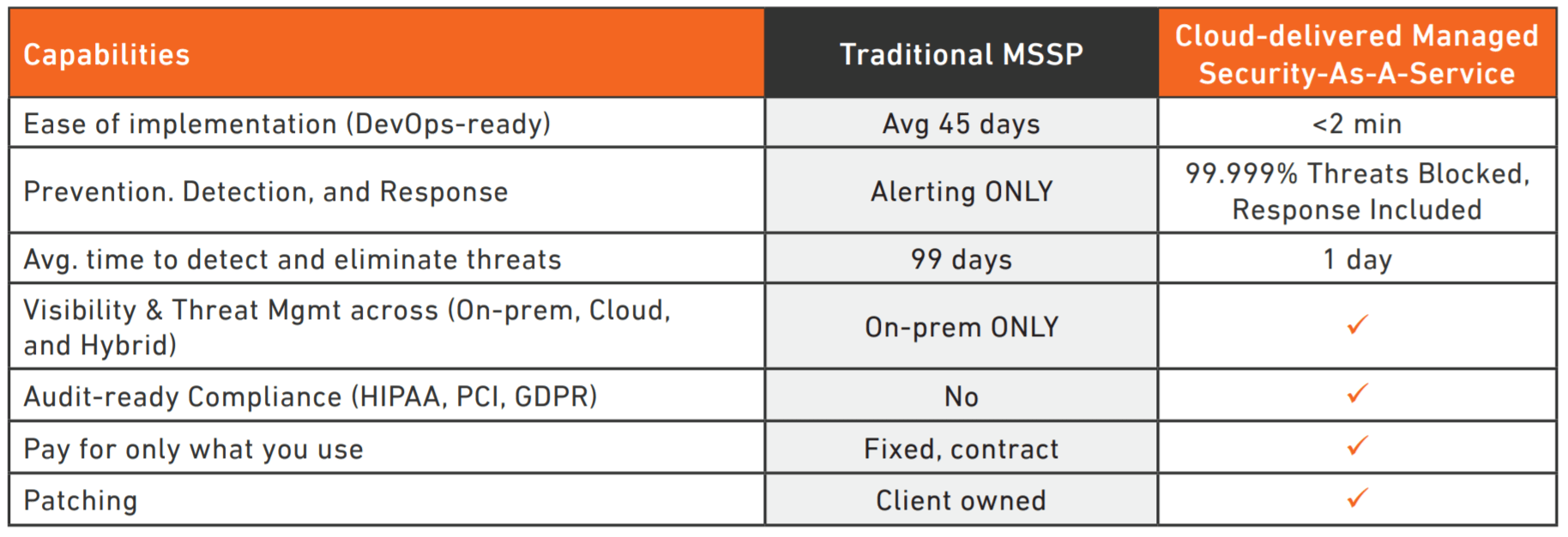
However, third-party security services shouldn’t all be viewed and treated the same. See our breakdown of capabilities delivered by traditional MSSPs v. SECaaS providers below.
Cost analysis and savings
Prior to deciding whether to engage a third-party SOC or create one in-house, organizations should conduct a cost analysis. Organizations planning to build their own should keep in mind that the national average for an analyst, incident responder, threat hunter and SOC manager is roughly $80,000 each, and the average price of a SIEM is about $50,000. Factoring in the bare-minimum requirement of four analysts, one incident responder, one threat hunter and one SOC manager in addition to a SIEM, that’s $610,000 just for starters.
Alternatively, outsourcing eliminates the burden of the aforementioned costs, as well as the need to purchase additional security products, pay for training and hire more staff. Not only can an organization offload time and resources to skilled cybersecurity professionals, they’re also saving that $600,000+ in overhead, which can be allocated to other departments or security resources.
Maintaining a company’s security is more than a full-time job. It truly requires dedicated 24/7/365 attention from a comprehensive, qualified team of cybersecurity experts. Despite the financial, personnel and technological resources of larger enterprises, the creation and maintenance of an in-house SOC can be daunting. When it comes to the cybersecurity of your company, we recommend putting down the hammer and leaving it to the pros.
To learn more if you should build or buy a SOC for your organization, download our whitepaper.