For the average person, the word “hacker” probably conjures up pictures of someone sitting behind a computer traversing the Dark Web. In the world of cybersecurity though, the word can also be applied to the researchers, penetration testers, and others working to improve IT security. Just as criminal cybersecurity hackers diligently work to penetrate your environment, ethical hackers are equally working to help organizations thwart them.
The differences and types of hackers
Colloquially, these two groups of hackers are broken up into two main categories: white hats and black hats. The names are believed to trace back to tropes in western films where cowboys with black hats were typically villainous, and those with white hats were heroic.
For cybersecurity pros, the gunfights are digital, but the bullets of malware and phishing are destructive nonetheless – leading to data breaches, downtime, and potential damage to the reputation of your business. The difference between the good and bad guys comes down to two elements: motives and limitations.
For black hats, the motive is often tied to greed and financial attainment, with attackers looking to compromise networks to steal sensitive information or hold it for ransom. In other cases, groups hack to disrupt the operations of various governments and businesses for personal or political reasons.
At Armor, we divide threat actors into three groups: Type A, Type B, and Type C. Type A are typically nation states and high-level attackers with substantial funding and expertise; they are almost impossible to detect. Type C (also known as commodity threats) are lower-level attackers, such as script kiddies and others that don’t have the knowledge to develop custom malware or exploits on their own. Type B would be in the middle in terms of sophistication and are typically targeted threats.
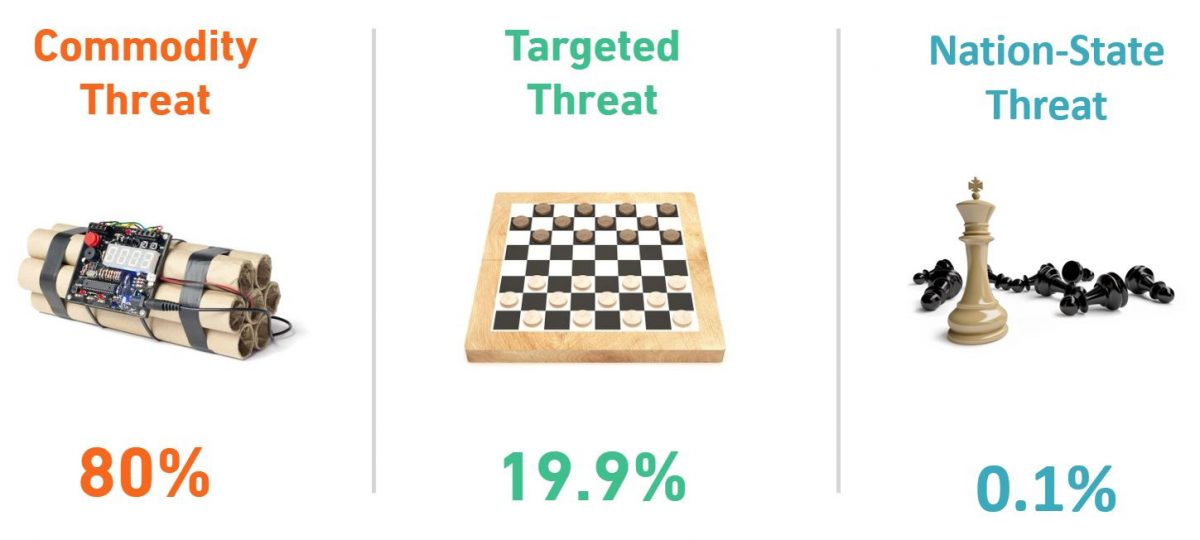
These categories, however, do not fully denote the level of damage attackers can do, as attackers with less sophistication can still have a significant impact. For example, while a Type C attacker may not be able to write his or her own exploit, that same attacker may be more than capable of scanning the Internet for misconfigured cloud environments with weak access controls. These attackers are rarely stealthy and typically focus on low-hanging fruit – organizations that are easy to compromise due to poor patching, leaving systems exposed on the Internet or other security mistakes.
A level higher on the spectrum are groups like Carbanak, which is reputed to have stolen approximately $1 billion over the course of several years. With a mix of phishing attacks and malware, the group successfully targeted financial organizations all over the world. In March, a person identified by authorities as the alleged leader of the group was arrested in Spain. The scope of the attacks of this type of cyber gang poses a serious threat to businesses.
Hacktivists often fall into the Type C category, though they can be Type B as well. Rather than steal data for monetary gain, these attackers are focused on making a statement, often through website defacement and distributed denial-of-service (DDoS) attacks. Perhaps the most infamous of these groups is the decentralized hacking collective Anonymous, which has been linked to numerous politically-motivated DDoS attacks over the course of the last decade.
At the most sophisticated level, spy agencies and groups backed by various governments target both each other as well as various types of businesses and organizations. Attributing these attacks is not always straight forward, as they typically are stealthy and may alter their methodologies or leave behind falsified artifacts in order to lead any investigators down a false trail. These hackers generally look to persist in the environments as long as they can, which allows them to potentially steal more data or take other actions while going undetected.
Living in the middle
While the white hats hack to defend and the black hats hack for personal gain, there is also a third group between these extremes known as “gray hats” – who sometimes violate laws and ethics but typically do so without the malicious intent of a black hat. An example of this would be a researcher who discovers a vulnerability and releases it publicly before a patch is released in order to embarrass a vendor or force a company into action. A well-publicized example of this would be when a security researcher hacked the Facebook page of Facebook CEO Mark Zuckerberg to force the company to fix a security flaw the researcher had discovered.
By violating Facebook’s policies against hacking without permission, the researcher crossed out of the realm of white hats, who accept that there are limitations governing their actions be they contractual, legal or merely ethical. White hats for example generally respect the idea of responsible disclosure, and only disclose information about vulnerabilities after the responsible party has had time to fix it – though what constitutes enough time can be subjective. A black hat of course, is not burdened by these concerns. Depending on their goals, they could either keep the vulnerability a secret for their own private use, sell it to an interested third party or simply release it for free.
Having a quick draw isn’t enough to beat the black hats of the digital world. It takes an effective mix of people, processes, and technology. In my next blog, I will examine where white hats fit in that mix, and why ethical hackers are important to the security of today’s organizations.