Updated as of 10:30 am CST, August 22, 2019
Armor Identifies Seven New Victims in Statewide Ransomware Attack
After identifying the cities of Keen and Borger, Texas as victims of the mass ransomware attack which hit Texas on August 16th, cloud security solutions provider Armor has identified seven new victim organizations. They include:
- Wilmer, TX
- Lubbock County, TX
- Bonham Police Department
- Grayson County, TX
- Graham Police Department
- Kaufman, TX
- Vernon Police Department
Wilmer, a small city in Dallas County with approximately 4,000 residents, seems to have been least prepared. According to an early morning local news reports from a Dallas TV station yesterday, their entire system was down, impacting the police department, water department and even library computers, said Mayor Dr. Emmanuel Wealthy Williams. The hackers demanded a ransom paid in bitcoin currency in exchange for release of the compromised data that’s been seized, according to the report. Mayor Williams went on to say that an assessment was expected to be completed Tuesday, but that it would probably be weeks before city operations are back to normal.
The second confirmed victim is Lubbock County. With a population of over 300,000, Lubbock County reports to have successfully fended off the attack due to a managed disaster and recovery plan.
“Our IT department was right on top of it,” said Lubbock County judge Curtis Parrish. “They were able to get that virus isolated, contained, and dealt with in a very quick manner so it did not affect any other computers or any other computer systems here in Lubbock County.”
In a local news outlet on August 20th, Police Chief Mike Bankston confirmed the Bonham Police Department was one of the government entities hit by the ransomware attack, but said no personal information has been compromised.
In addition, according to a local news report on August 20th, some services in Grayson County were shut down for less than 24 hours due to the attack, but the county says all systems are back online and there are no ongoing issues.
The Graham County Police Department may now have the dubious honor of receiving the highest ransom demand of 2019 so far. One of their servers was knocked completely out, while another was held for ransom demanding $5,000,000 according to a local news outlet.
The City of Kaufman, TX
The city of Kaufman, with a population of just over 7,000, stated on their Facebook page on August 19th, that all of their computer and phone systems were down and their ability to access data, process payments, etc. is greatly limited.” Interestingly, the Kaufman Police Department suffered a ransomware attack in 2018 and sought assistance from MonsterCloud, a ransomware recovery firm most notably mentioned in a 2019 ProPublica article on ransom payment methods.
Vernon Police Department
According to a local news outlet, Vernon, Texas Police Chief reported that the city had also been hit. “Monday morning about 2:30 a.m. my computers were hit with what we’ve identified as a ransomware virus which has shutdown our system for the time being,” Vernon Police Chief Randy Agan
The chief said this shutdown has not affected their day to day police operations but it has made them go old school.
“Handwritten reports we have to go in and fill in all of the pre-detects boxes and stuff on our reports that we have that the computers automatically fill in for us,” Agan said. “So, it’s a little bit more in-depth and it’s a little bit more repetitive because we don’t have the master main files or the list of our charges.”
On Tuesday the Texas Department of Information Services revised the number of victims to 22, but has yet to release the names of affected city and county governments. Despite the radio silence, news is beginning to reach citizens as government services are suspended and payments are delayed.
67 U.S. Municipalities Hit by Ransomware Attacks in 2019
There have been a total of 67 publicly reported ransomware attacks since January 2019 against municipalities, including the 22 in Texas, reported Armor. Armor has tracked 135 U.S. organizations (Armor just discovered Glenwood District in Glenwood, Iowa and Bayview Dental in North Branch, Minnesota) as have being infected with ransomware since the beginning of the year, However, these are only incidents which have been reported publicly. Armor is confident that there are hundreds of other organizations which have been victims of the ransomware threat.
Why are So Many Municipalities Hit by Ransomware?
According to Armor’s Chris Hinkley, sr. security researcher with Armor’s Threat Resistance Unit (TRU) team, when asked why so many municipalities are targets, he stated: “A ransomware attack on a municipal government can be crippling to a city. Holding the digital data of a city can cause havoc in all aspects of a city’s day-to-day operations; from trash pickup to correctional facilities. The enormous impact of city’s operations, like 911, courts, police and fire, and even non-emergency services (like paying one’s utilities and property taxes online, processing real estate lien certificates, etc. ) creates a huge sense of urgency and anxiety. With the high-level of urgency and potentially mission-critical value of the data being held hostage, the threat actor(s) are more likely to get paid, and at a higher amount than if they attacked another target.”
Hinkley also added, “Additionally, governmental agencies are generally constrained financially, which usually means they have fewer security protections in place than a private organization. So, between housing critical data and having less security, makes cities a potentially softer target.”
Updated as of 4:30 pm CST, August 21, 2019
Sixty-Seven Municipalities Fall Victim to Ransomware in 2019, Reports Armor
Cloud security solutions provider Armor has identified the City of Borger, Texas and Keene, Texas as being among the 22 local Texas government organizations hit by ransomware on August 16th. There have been a total of 67 publicly reported ransomware attacks since January against municipalities, including the 22 in Texas, reported Armor. Armor has tracked 133 U.S. organizations which have been infected with ransomware since the beginning of the year, However, these are only incidents which have been reported publicly. Armor is confident that there are hundreds of other organizations which have been victims of the ransomware threat.
Ransomware Attack Prevents Citizens of Borger, Texas from Paying Utility Bills, Accessing Birth and Death Certificates….
According to a public statement issued by the City of Borger on August 19th, currently, Vital Statistics (birth and death certificates) remain offline, and the City is unable to take utility payments or other payments. As a result the City of Borger is not assessing late fees and no services will be shut off. The city also went on to say: “This attack has impacted normal City business and financial operations and services, however, the City has implemented its continuity of operation plans and the City continues to provide basic and emergency services (Police, Fire, 9-1-1, Animal Control, Water, Wastewater and Solid Waste Collection). The City continues to actively work with responders to bring our computer systems back online and regain full operations. Responders have not yet established a time-frame for when full, normal operations will be restored.”
Ransomware Attack Hits Keene, Texas Preventing Credit Card Payments by Residents
Keene, Texas, a city of approximately 6,400 residents, posted on their Facebook page that they too had been hit by the coordinated ransomware attack of August 16th. They stated the following:
“Keene is working with law enforcement to resolve a cyber incident that impacted servers state-wide. Because this is an investigation, we can’t share much.
Here’s what you need to know:
• No credit card payments or utility disconnections for now
• Our drinking water is safe
• Check back here for updates”
States with Most Ransomware Incidents Affecting Municipalities
As of today, Texas leads the nation in the number of municipalities which have fallen victim to ransomware, they are currently up to 29 victims, followed by Georgia with 9, Florida with 8, along with New York, Ohio with 7, etc. See the full list below.
Texas: 29 (with 22 announced August 16)
Georgia: 9
New York: 8
Florida: 8
Ohio: 7
California: 7
Pennsylvania: 6
Washington: 5
133 U.S. Organizations Publicly Reported Victims of Ransomware in 2019
Out of the 133 victim organizations compromised by ransomware in 2019 in the U.S. (See the full list of victim organizations at the end of this document), municipalities make up the largest portion. This is followed by healthcare organizations and school systems. The remaining victims fall into a variety of different industries including entertainment, law enforcement, etc. (See the full victim list at the end of this document and the attached attack map showing their geographical location).
67 attacks on municipalities
23 attacks on healthcare systems
16 school systems, colleges or universities
7 law enforcement agencies
3 managed service providers (MSPs)
3 radio stations
2 media companies
2 large airport
1 synagogue
1 charity
9 other
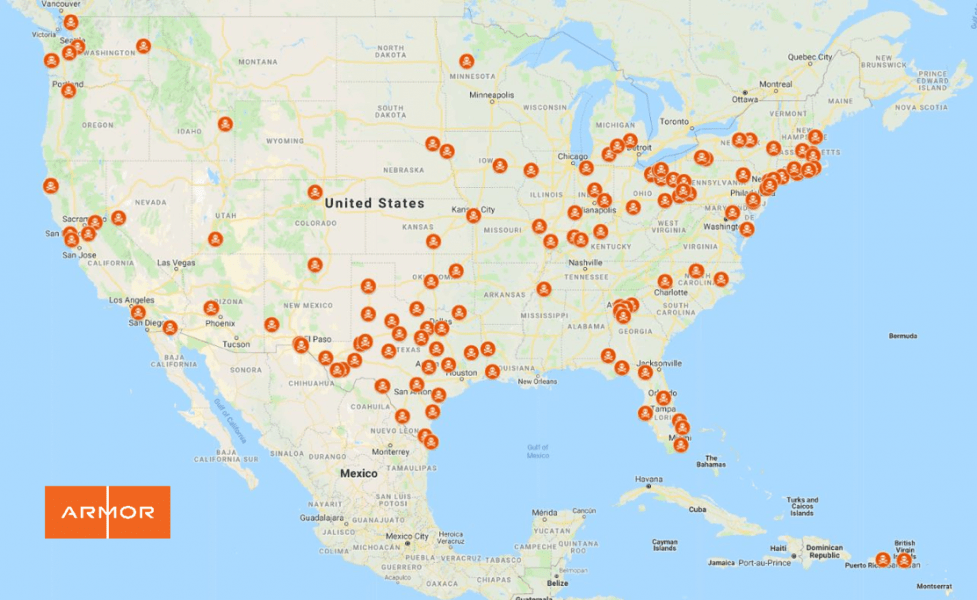 Locations of 2019 Publicly Reported U.S. Ransomware Victim Organizations
Locations of 2019 Publicly Reported U.S. Ransomware Victim Organizations
The High ROI of Ransomware
Compared to the amount of money a ransomware operation can generate, the cost of getting into the ransomware game is negligible. Take for example, the threat actor (s) that hit Riviera Beach, Florida, they made off with $600,000 in one attack. The threat group that hit Lake City, Florida with the Ryuk ransomware collected $460,000 in one haul.
To get an idea of how inexpensive ransomware and ransomware- as-a -service (RaaS) solutions are being sold for on the Underground Hacker Markets, Armor’s Threat Resistance Unit (TRU) went into the Dark Web and found the following ransomware and RaaS offerings being advertised.
| Generic Ransomware | $225 |
| Generic Ransomware | $660 |
| Inpivx Ransomware | Ransomware +Panel +Tutorial= $500
Ransomware-only-$300 Panel-only – $200 |
| Ranion-(RaaS) | 12 months $900
6 months $490 1 Month $120 |
| Megacortex Ransomware | $1,000 or €1,000 +10% of ransom |
Inpivx Ransomware and Panel for Sale

The creators of the Inpivx ransomware offer to sell the source code to their panel, the ransomware and a tutorial for only $500. Or buyers could buy the components separately.
Inpivx pricing:
- Inpivx Ransomware + Panel + Tutorial = $500
- Inpivx Ransomware-only – $300
- Inpivx Panel-only – $200
Popular Ransomware Families
According to news reports, the ransomware which hit the local Texas governments is called .JSE ransomware. It is also sometimes referred to by anti-virus vendors as Nemucod, the downloader trojan which has been seen dropping the ransomware onto infected computers. This ransomware family is only one of hundreds of different ransomware families identified by Armor’s (TRU) research team and by the security research community. Other notable ransomware families which are making their mark in 2019 include:
- Ryuk is one of the most prevalent families of ransomware used in 2019 attacks (of those widely reported); In July, the FBI stated 100 companies were hit from Ryuk in the last 12 months
- In 2019, LockerGoga has been cited as being one of the prevalent ransomware threats to hit organizations in UK and Europe
- Other sporadic mentions of ransomware families relating to 2019 US attacks include: Dharma (Crysis), Cryptomix and MegaCortex; Robbinhood (City of Baltimore and Greenville, NC)
- GandCrab was by far the leading ransomware in 2018, by March 2019 there were 9 variants; in June 2019 GandCrab authors purportedly “retired” claiming $2 billion in collections and a decryption key was released by the FBI released in July 2019
- Sodinokibi/Sodin/REvil may be RaaS replacing GandCrab according to several security researchers.
An Ounce of Prevention is Worth a Pound of Cure
From the rash of ransomware attacks which have occurred this year, if there is any lesson to be learned and only one preventive measure which can be taken is that organizations must utilize OFFLINE BACKUP STORAGE of all critical data, applications and application platforms. They must ensure that these are backed up, password- protected and air gapped from the Internet and ensure that they have multiple copies.
Other Key Ransomware Protection Tips Include:
- White Listing Solution – limits the use of applications and processes that are allowed to run in your environment by providing a short list of approved applications and processes. Like a VIP List for your PC, if it’s not on the list, it’s not allowed.
- File Integrity Monitoring—Monitors your IT environment 24x7x365 for changes to critical OS, files and processes such as directories, registry keys, and values. It also watches for changes to application files, rogue applications running on the host and unusual process and port activity, as well as system incompatibilities.
- Practice Least Privilege Access Control –ensure the user has the least privilege for their job. This also applies to services.
- Audit/Penetration Testing from Independent, Third-Party Experts—to ensure that you are implementing best practices.
- IP Reputation Monitoring/Blocking—blocking bad known bad infrastructure and actors
- Continuous Security Awareness Training – educate employees about current and emerging cybersecurity risks and phishing emails. Effective training should actively engage employees and include policies concerning the correct response to suspected phishing attempts.
- Endpoint Protection Solution – includes protection, detection and response capabilities for laptops, workstations and mobile devices. Utilizes antivirus (AV) and antimalware (AM) to block cyber attacks. It is also used to quickly detect and remediate any malicious activity or infection that has made its way onto the endpoint.
About Armor
Armor is a leading global cloud security-as-a-service provider headquartered out of Dallas, Texas. Armor protects the cloud and on-premise data of 1,200 organizations across the globe. Armor’s TRU team originally discovered that the Robbinhood ransomware variant used against the City of Baltimore in May did not contain the NSA-created Eternal Blue exploit. Although, it is possible that Eternal Blue was used by the ransomware criminals as a separate component to spread the Robbinhood ransomware. The TRU team also discovered that Robbinhood was structured as ransomware-as-a-service.